UTCTF 19 [ Regular Zips ]
To start with, UTCTF 2019 had pretty high scores for every challenge ie. The points were ranged from 100 to 2000.
And They were all fun to solve, But I personally liked Regular Zips as I learn a lot about Regular Expressions and ofcourse python’s awesomeness. XD
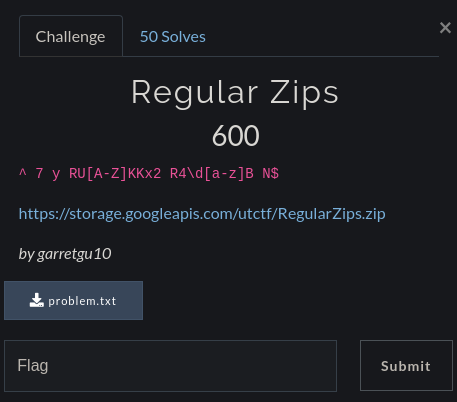
Download RegularZips.zip & problem.txt
Being a 600 pts challenge, it was somewhat a medium level challenge.
Thanks to my friend @HimanshuKr who helped me with this challenge.
So I started with the given regular expression in the problem.txt which was provided to us. Also it was the same regex which was in the challenge description.
We were also given a zip which was obviously encrypted and we had to decrypt by brute-forcing it against some words that satisfy the regex.
I quickly used my google foo skills to search for a Regex library which can be used with python to generate those words.
Oh there’s a perfect library for our work => exrex
Install it using :
1 | pip install exrex |
And I shooted Sublime to make a wordlist and brute-force at the same time using python :
1 | import exrex |
And we got our password…
But Be careful with spaces and tabs !!
1 | Password found: 7 y RUHKKx2 R47gB N |
But that’s not enough, we have a long journey ahead. lols..
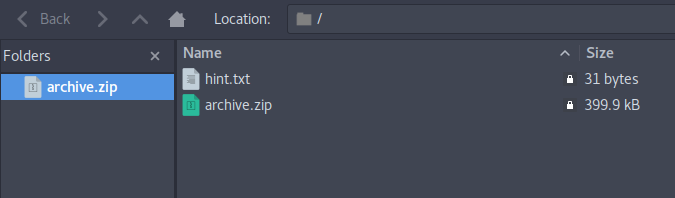
So after extracting it we get another zipfile as archive.zip and a hint.txt file which contains another regex sadly.
So we can just write a script to extract all of the archives until we are left with none of them. I used zipfile library in python to workaround with zip files in python and added some colors to make the automation process more fun.
I created a new directory and placed this script along with RegularZips.zip and Problem.txt.
1 | import os |
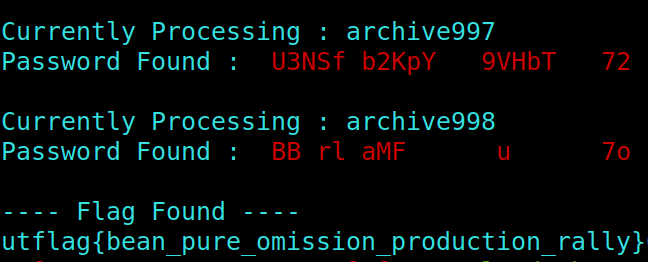
And To our Surprise …
There was a flag.txt in archive998.
The Flag was :
1 | utflag{bean_pure_omission_production_rally} |
Wasn’t it Sw33t.
Don’t hesitate to leave a feedback in the comments section and Subscribe if you want to stay updated with other CTF’s writeups and walkthroughs.
Keep Waiting for my next writeup.
Till then Keep Escalating the Priveleges and Happy Hacking !!