FireShell CTF [babycryptoweb]
To get started I want to tell my experience regarding this CTF.
Fireshell CTF was both Fun and Weird..
It had challenges on some uncommon categories like PPC and RECON which were fun.
But Let me get you straight to the point. It was bit confusing as very less hints were given.
So To begin with, BabyCryptoWeb was too easy but it was difficult for those who overlook things. XD
It was named so as there were two methods of solving this challenge (Web and Crypto).
Seems Interesting
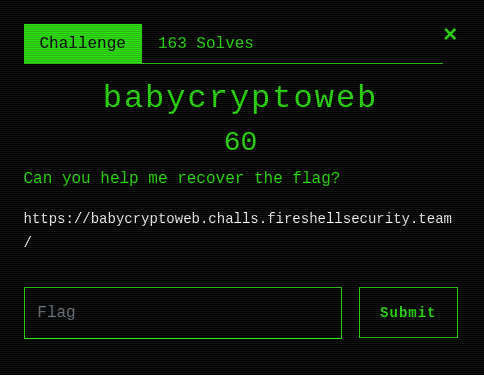
I started by gathering some info through the code which was given to us on the webpage.
1 |
|
Then I copied all the code in the $code variable on my local machine and made a file as babyweb.php.
As all the challenge requires is to understand the code ..
It’s a bit obvious .LOLs
1 |
|
I ran the php code on my terminal and got some weird looking text :(
Then I tried changing $kkk but nothing helped..
The code decrypts the base64 encoded string which is indeed our flag.
Then there is a for loop that decides the value for $ch and $kch using substr.
And at last $ch is concatenated to $res
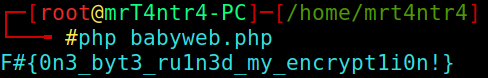
And at last after understanding the code I changed
1 | $ch=chr(ord($ch)+ord($kch)); |
TO
1 | $ch=chr(ord($ch)-ord($kch)); |
and if you noticed I changed the (+) to (-) operator and It worked like a charm.
2nd Method
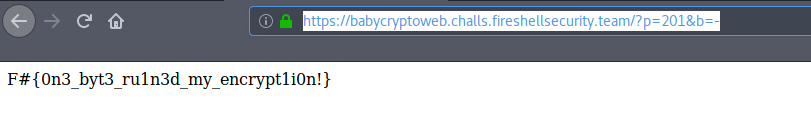
I also studied the code with some GET_ functions and found that it is requiring us to set both parameters p and b ..
I observed that p specifies that which place of code we can change and b specifies what we can change with..
I think you are smart enough to solve it now..
I just checked the Length of the $code string till ‘+’ as we have to change that.
1 | code = '$kkk=5;$s="e1iwZaNolJeuqWiUp6pmo2iZlKKulJqjmKeupalmnmWjVrI=";$s=base64_decode($s);$res="";for($i=0,$j=strlen($s);$i<$j;$i++){$ch=substr($s,$i,1);$kch=substr($kkk,($i%strlen($kkk))-1,1);$ch=chr(ord($ch)+'' |
OUTPUT:
202
I simply tried this and BOOMYa :) !!