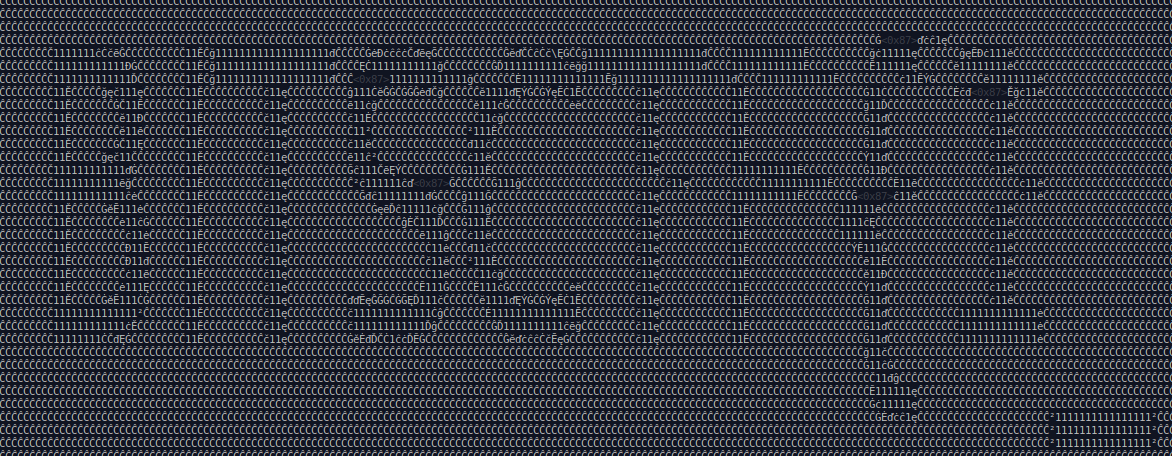BITS CTF 2019
BitsCTF 2019 had somewhat medium and easy challs too.
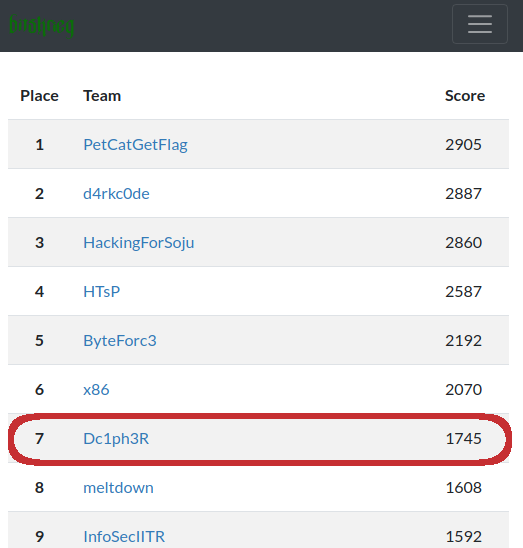
At the end my team was finally able to secure a rank in the Top 10 with 1745 pts.
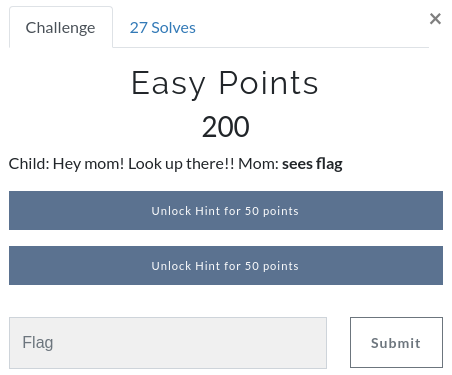
EasyPoints (Web)
As the challenge says to Look UP.
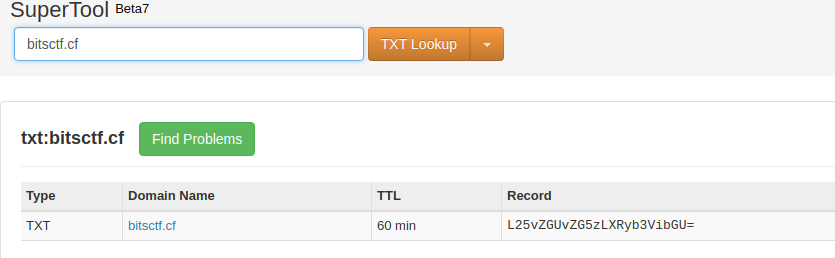
I quickly use mxtool to carry a txt record lookup.
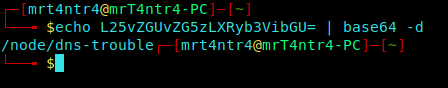
I found a base64 encoded string, Yip33 !!
That was not enough :(
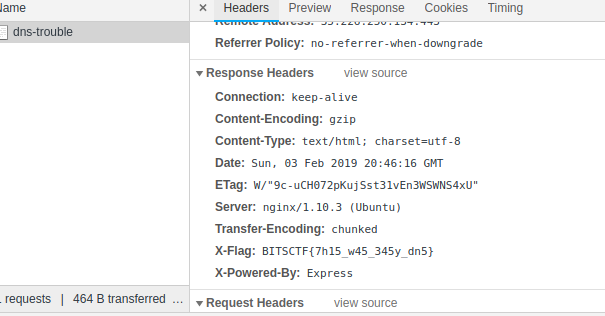
I moved on !! and observed the Response Headers.
One of them X-Flag contained the flag…
SPIFFED (Forensics)
I checked what type of file it was.. but sadly that didn’t help …
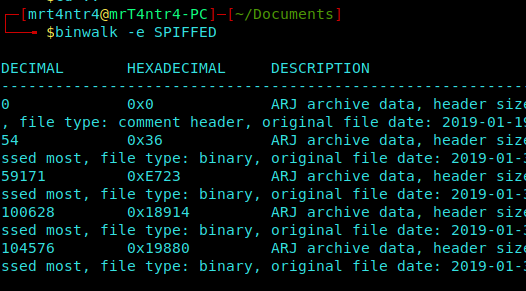
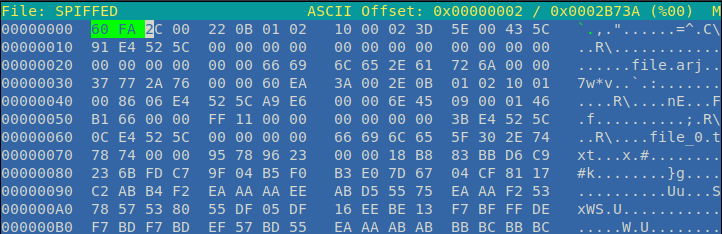
And I moved on with hexeditor , but nothing seemed interesting so I checked for some embedded files using binwalk and got the following output.
But wait I didn’t get the _extracted folder. I can smell the hardness of level now !!
I checked the headers if they were correct for the ARJ archieve data file.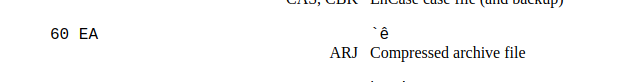
And to my surprise it was wrong…
After correcting the header using hexeditor I navigated into the _extracted directory.
And I observed that all files were containing some gibberish text.
After some tinkering around and decreasing my font size I got to see the FLAG ..
B00mYa!! Lets the drinks go on..
And the flag was BITSCTF{I_L0v3_D0g5_D0_Y0u??}
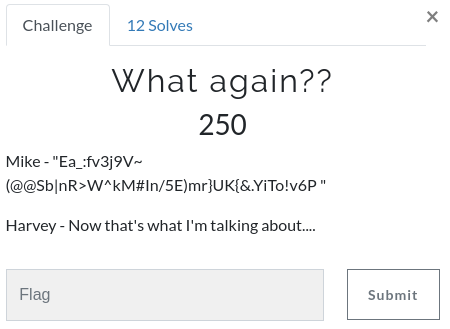
WhatAgain (Crypto)
This task was completed by my teammate..
So all the credit goes to him :P
After struggling for a while to find what kind of encryption is it..
There were many discussions regarding this question XD
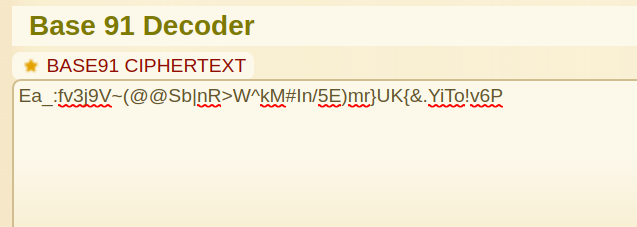
At last it was a simple Base91 encoded String !!!
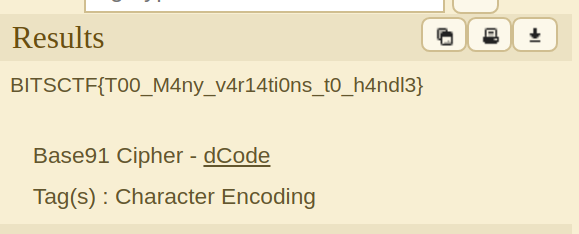
We used Base91 Decoder from dcode
and got flag as the Result.